In this new decade, the average consumer is persuaded to use the credit card on the Internet for purchases, raising the risks of
cyber theft. Insurance policies are offered by most credit cards companies and former hackers are hired by the industry to design improved security measures.
Cyber attacks become more frequent and destructive and kids using automated programs that perform functions they could not perform on their own, conduct many of these actions, hitting big companies and causing severe financial losses. The denial-of-service attack becomes a tool of war and the attacks are designed to paralyze websites, financial networks and other computer systems by flooding them with data from outside computers.
Alongside with these criminal attacks against banks and every wire dependent industries, there a rise of the
cyber terrorism threat. This is the 9/11 decade and the attacks in the United States spawn diverse reactions from different groups, with the FBI issuing warnings of potential terror attacks through the Internet. Some believe that the threat is real and possible at any given moment, while some countered that it is not that easy, and is almost impossible with all the existing security systems.
Historical Landmarks
2000
Michael Calce, a 15-year-old Canadian with the handle "
MafiaBoy", launches a series of DoS attacks against huge companies with high levels of security and numerous e-commerce sites. Amongst those attacked are computer manufacturer Dell, media giant CNN, and shopping sites Amazon and Ebay. In order to do so, MafiaBoy gains illegal access to 75 computers in 52 different networks and plants a DoS tool on them which he then activates and uses to attack several Internet sites causing about $1.7 billion losses.

Russian hackers penetrate
Microsoft Corporation and view portions of the source code for key products such as Windows and Office suite.
Yahoo, eBay, Amazon and dozens of other high-profile Web sites go offline for several hours because of a series of so-called
Distributed Denial-of-Service (DDoS) attacks. Investigators later discover that the attacks were orchestrated when the hackers co-opted powerful computers at the University of California-Santa Barbara.
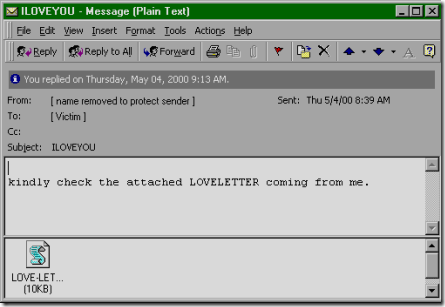
The
I LOVE YOU worm, also known as Love Letter and Love Bug worm, starts spreading from Manila and within ten days, over fifty million infections have been reported. It is a computer worm written in VBScript by an AMA Computer College student for his thesis.
 Vitek Boden
Vitek Boden, a disgruntled employee, hacks the Maroochy Shire Council's sewage control system in Queensland, Australia and releases millions of gallons of raw sewage on the town waterways.

A Russian cracker attempts to extort $100K from online music retailer
CD Universe, threatening to expose thousands of customers' credit card numbers. He posts them on a website after the attempted extortion fails.
 Hactivists
Hactivists in Pakistan and the Middle East deface Web sites belonging to the Indian and Israeli governments to protest against oppression in Kashmir and Palestine.
A news release issued by
Internet Wire, and reported by Bloomberg and other news organizations, causes Emulex stock to plunge from $110 a share to $43 on the NASDAQ exchange in minutes. A former Internet Wire employee, believed to have authored the bogus story, faced charges and is alleged to have pocketed $241,000 short-selling Emulex shares that day.
Kevin Mitnik is released from prison.
2001
Microsoft is targeted in a new type of attack against the
Domain Name Servers. In this DoS attack, the DNS paths taking users to Microsoft's web sites are corrupted and millions of users are unable to reach Microsoft web pages for two days.
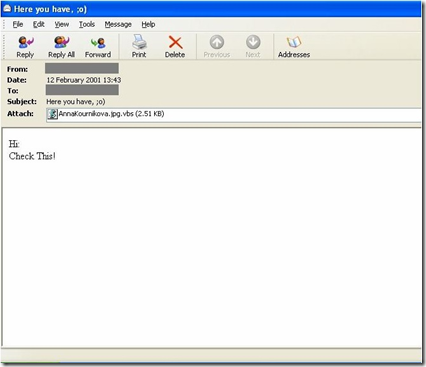
A Dutch cracker releases the
Anna Kournikova virus. Promising digital pictures of the young tennis star, the virus mails itself to every person listed in the victim's Microsoft Outlook address book. Although being relatively benign, the virus frightens computer security analysts, because it appears to have been created using a software "toolkit" that allows even the most inexperienced user to create a computer virus.
 Dmitry Sklyarov
Dmitry Sklyarov, a Russian programmer, is arrested at the annual Defcon hacker convention being the first person criminally charged with violating the Digital Millennium Copyright Act (DMCA).
Code Red, the first polymorphic worm, infects tens of thousands of systems running Microsoft Windows NT and Windows 2000 server software, causing an estimated $2 billion in damages. The worm is programmed to use the power of all infected machines against the White House web site at a predetermined date.
The
9/11 World Trade Center and Pentagon terrorist attacks spark US lawmakers to pass a barrage of anti terrorism laws (including the Patriot Act), many of which group hackers with terrorists.
Microsoft and its allies vow to end "full disclosure" of security vulnerabilities by replacing it with "responsible" disclosure guidelines.
Debuting just days after the Sept. 11 attacks, the
Nimda virus wreaks havoc on the Internet infecting hundreds of thousands of computers around the world. The virus is considered one of the most sophisticated, with up to five methods of infecting systems and replicating itself.
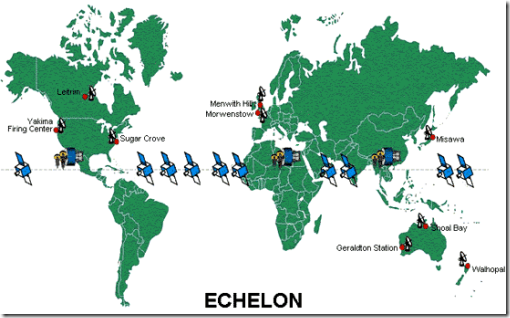
EU publishes report on its investigation of the
ECHELON system, purportedly used by the US, UK, Canada, Australia and NZ to spy on radio, telephone and Internet communications. Meant for military and defense use, there is suspicion it is being used to invade personal privacy and for commercial spying.
A Chinese fighter collides with an American surveillance plane and tensions in
Chinese-American diplomatic relations rise. US and Chinese hackers engage in web defacement skirmishes.
Melissa virus author David L. Smith, 33, is sentenced to 20 months in federal prison.
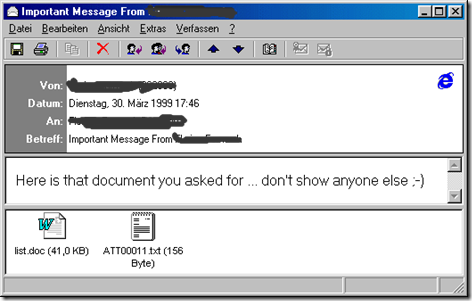
FBI establishes a
fake security start-up company in Seattle and lures two Russian citizens to U.S. soil on the pretense of offering them jobs, then arrests them. The Russians are accused of stealing credit card information, attempting to extort money from victims, and defrauding PayPal by using stolen credit cards to generate cash.
2002
U.S. Naval War College sponsors the
Digital Pearl Harbour exercise in which analysts act as terrorists and simulate a large scale attack on several infrastructures. Conclusions are that such an attack would not result in catastrophic events and deaths but can cripple communications in heavily populated areas.
The
Klez worm becomes the biggest malware outbreak in terms of machines infected. It sends copies of itself to all of the e-mail addresses in the victim's Microsoft Outlook directory, overwrites files and creates hidden copies of the originals. The worm also attempts to disable some common anti-virus products and has a payload that fills files with all zeroes. In spite all of this it causes little monetary damage.
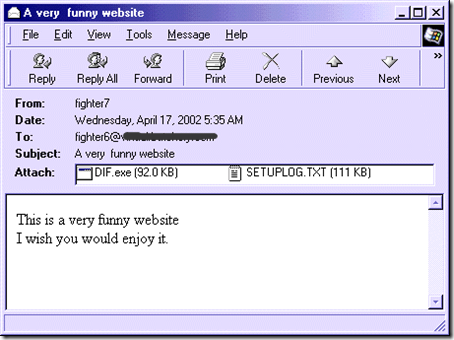
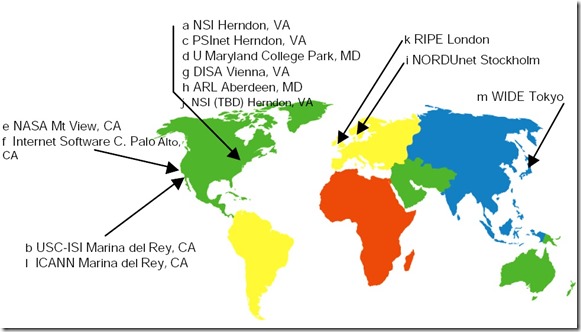
A DDoS attack hits all 13 of the
root servers that provide the primary DNS services for almost all Internet communications. Nine servers out of these thirteen are jammed but Internet users experience no slowdowns or outages because of safeguards built into the Internet's architecture. However, the attack raises questions about the security of the core Internet infrastructure.
2003
The
SQL Slammer worm infects hundreds of thousands of computers in less than three hours generating chaos on businesses worldwide. It holds the ranking as the fastest-spreading computer worm ever.
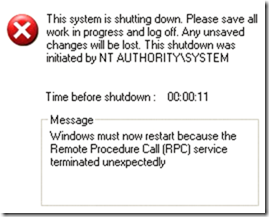
MS Blaster worm and variants (Welchia) are released. The worm may have contributed to the cascading effect of the Aug. 14 blackout, that affected an estimated 10 million people in Ontario and 45 million people in eight U.S. states.
A worm disables critical safety systems at a
nuclear power plant in Ohio.
Howard Carmack, also known as the
Buffalo Spammer is arrested in New York after sending 825 million e-mails, fraudulently using the identities of two people from the city of Buffalo, as well as hundreds of aliases.

The hacker group
Anonymous is formed.
A Russian hacker group known as the
Hang-Up Team builds a Web site featuring administrative tools for attacking U.S. financial institutions.
2004
North Korea claims to have trained 500 hackers to crack computer systems in South Korea, Japan and their allies.
The
My Doom worm claims to be a notification that an e-mail message sent earlier has failed, and prompts the user to open the attachment to see what the message text originally said. It is basic social engineering to persuade recipients to open attachments containing the virus.
From their lair in distant Romania, a group of hackers penetrate the computers controlling the life support systems of a
research station in the Antarctic. The extortionists confront the 58 scientists and contractors with the sudden prospect of an icy death if their money demands are not met. The culprits are stopped before any damage is done.
After 4 years of investigation, US Secret Service's Operation Firewall discovers a network of over 4,000 members communicating through the Internet and conspiring on a series of crimes. The Secret Service seizes control of the
Shadowcrew web site and arrests people in eight states and six countries.
Sven Jaschan, a 18 year old German student, releases the
Netsky virus. It infects millions of computers around the world and disables the Delta Air Lines computer system, causing the cancellation of several transatlantic flights. Jaschan is arrested after a three-month hunt, during which Microsoft places a $250,000 bounty on the hacker's head. Multiple variants of the virus keep spreading in the following months.
 Sanford Wallace
Sanford Wallace, "The Spam King", is investigated by the FTC and fined four million dollars.
Shawn Carpenter, a Sandia National Laboratories employee, discovers an extensive series of infiltrations into US military security companies such as Sandia, Lockheed Martin, Redstone Arsenal and even NASA. FBI names these attacks
Titan Rain and labels them as Chinese in origin, although their precise nature remains unknown.
2005
A
Netcraft survey estimates more than 60M web sites online.

Hackers gain access to
Paris Hilton's T-Mobile Sidekick smartphone and post her photos and phone numbers online.
Bank of America has 1.2M names and Social Security numbers stolen.
FBI's e-mail system is hacked.
The
Samy worm makes everybody Samy's friend at MySpace.
Tel Aviv Magistrate's Court imprisoned several people from some of Israel's leading commercial companies and private investigators suspected of commissioning and carrying out industrial espionage against their competitors, which was carried out by planting Trojan horse software in their computers.
Jeanson James Ancheta, is taken into custody by the FBI. He allegedly is a member of the
Botmaster Underground, a group of script kiddies mostly noted for their excessive use of bot attacks and propagating vast amounts of spam.
2006
Ancheta receives a 57-month prison sentence, and is ordered to pay damages amounting to $15,000 to the Naval Air Warfare Center in China Lake and the Defense Information Systems Agency, for damage done due to DDoS attacks and hacking.

Turkish hacker
iSKORPiTX successfully performs the largest defacement in Web History, at the time, hacking 21,549 websites in one single shot.
US Air Force announces plans to create a
Cyber Command to handle
cyberwarfare and network defense.
Hackers break into
Department of Homeland Security computers, install malware, and transfer files to a remote Chinese-language Web site; Unisys (the contractor) is charged with covering up the intrusion.
Hacker accesses Linden Lab's
Second Life database and steals unencrypted account names, real life names and contact information, and encrypted passwords and payment data.

A bank machine in
Virginia Beach is reprogrammed to dispense $20 bills in place of $5 bills. The machine was left this way for 9 days before someone mentioned the discrepancy to the store clerk.
An
Alabama nuclear power plant is shut down due to excessive network traffic.
A series of cyber attacks is launched against numerous organizations including governments and defense contractor. This will later be known as
Operation Shady RAT.
In the war against Hezbollah, Israel alleges that
cyberwarfare was part of the conflict, where the
Israel Defense Forces (IDF) intelligence estimates several countries in the Middle East used Russian hackers and scientists to operate on their behalf.
According to a Gartner study, the 1.5M Americans were victims of
identity theft in 2006.
2007
Estonia is subjected to a massive cyberattack by hackers inside the Russian Federation in the wake of the removal of a Russian World War II memorial from downtown Tallinn. In a very brief period of time, a variety of methods are used to take down key government websites, news sites and generally flood the Estonian network to a point that it is useless, disrupting the use of websites for 22 days.
Nearly all Estonian government ministry networks as well as two major bank networks are knocked offline and the whole attack is considered as the perfect example of how vulnerable a nation can be to cyberattacks during a conflict.
The Chinese government and military are accused of hacking other nations' networks, including US pentagon networks, and German and UK government computers.
Russian Business Network (RBN) offers bulletproof hosting, allowing sites which host illegal content to stay online despite legal takedown attempts.

Russian gang uses
RBN hosting and SQL injection to penetrate US government sites.
Israel launches an airstrike on Syria dubbed
Operation Orchard. U.S. industry and military sources speculate that the Israelis may have used cyberwarfare to allow their planes to pass undetected by radar into Syria.
The U.S. Department of Homeland Security conducts the "
Aurora Generator Test" at Idaho National Laboratories, which shows that a cyberattack on an industrial-control system can damage a machine. The test involves the remote accessing of a generator control station by a foreign hacker and it causes a large diesel generator to shudder, hurl shards of metal, and emit smoke before dying altogether.
FBI Operation
Bot Roast finds over 1 million botnet victims.
FBI Operation
Bot Roast II: 1 million infected PCs, $20 million in losses and 8 indictments.
Paul Strassmann, former senior U.S. information security official, estimates that there are over 730,000 compromised computers "infested by Chinese zombies." This is a clear reference to possible effects of recent cyberattacks that left behind malicious software that can be activated later.
2008
A video of Tom Cruise espousing his belief in the Church of Scientology is leaked to YouTube and the Church attempts shut it down. As a response to this, the group calling itself 'Anonymous' starts "
Project Chanology", an anti-Scientology movement aiming to systematically expel The Church from the internet. Over the following weeks, Scientology websites are intermittently knocked offline and private documents are stolen from Scientology computers and distributed over the Internet. The Church of Scientology moves its website to a host that specializes in protection from denial-of-service attacks but the cyber attacks and hacks against the celeb-addled religion continue until today.
Hundreds of government and corporate Web sites in
Lithuania are hacked, and some are covered in digital Soviet-era graffiti, implicating Russian nationalist hackers.
MySpace and
FaceBook private pictures exposed on-line using URL manipulation.
A computer hacker leaks the personal data of
6 million Chileans (including ID card numbers, addresses, telephone numbers and academic records) from government and military servers to the internet, to protest Chile's poor data protection.
Senior CIA analyst
Tom Donahue, speaking at a conference, publicly acknowledges that attackers have targeted power-grid computers worldwide, causing at least one widespread electrical outage.
Russian forces invade
Georgia, preceded by cyberattacks on Georgian government and business websites and network infrastructure, disabling the country's Web-based communication with the outside world.
Joel Brenner, national counterintelligence executive, calls China's cyber militia formidable. He says the Chinese operate both through government agencies and sponsoring organizations, which mount attacks on the US in "volumes that are just staggering."
The
Obama and McCain presidential campaigns, during their run for the 2008 presidency, are heavily attacked. What is first thought of as simple cyberattacks on the computers used by both campaigns is discovered to be a more concentrated effort from a "foreign source" that violates emails and sensitive data. The FBI and secret service swooped in and confiscate all computers, phones and electronics from the campaigns. There are no final conclusions but the rumors point to the usual suspects: China or Russia

Unknown foreign intruders use "thumb drives," portable memory sticks, to infect DOD networks. Inserted into a military laptop in the Middle East, the malicious code on the drive creates a - according to Deputy Secretary of Defense William Lynn - "digital beachhead, from which data could be transferred to servers under foreign control." The attack acted as another reality check in security, and results in what one Pentagon official would later call the "
most significant breach of US military computers ever."
The
Conficker worm starts infecting PCs, quietly recruiting them into the world's largest botnet, responsible for distributing viruses, malware and taking part in massive denial of service attacks on behalf of their masters. The source of the worm and its many variants is still unknown, although some researchers believe it originated in the Ukraine. The worm is still active today in spite of all the efforts made to eradicate it. Microsoft has a standing bounty of $250,000 for information leading to the arrest of its creators.
Trusted payments processor
Heartland Payment Systems is victim of a plot to steal credit and debit card numbers. By secretly infesting the company's computer network with spyware, a criminal gang is able to steal over 100 million individual card numbers and this episode ended up costing them around $140m.

Grocery retailer
Hannaford Bros suffers a four-month long breach of their security. During this period, over 4.2 million credit and debit card numbers are exposed, along with other sensitive information. The costs are estimated in $252m.

One of the principal hackers involved is
Albert Gonzalez, who had also hacked Heartland Payment Systems as well as TJ Maxx. Gonzales committed his crimes between 2005 and 2008. Ironically, he was hired as a U.S. Secret Service informant which earned him $75,000 annually during that time frame. The Secret Service was unaware of his activities until 2008.

The hacker called his scheme "
Operation Get Rich or Die Tryin'" and was achieved through the installation of malware on store servers, which stands in contrast to the more common tactic of hacking company databases. To steal the debit and credit card information, he used a packet sniffer to obtain transaction data directly from retailers. The data was routed to servers leased in the Ukraine and Latvia. He then distributed the information to Maksym Yastranskiy, a Ukrainian card seller. Yastranskiy was captured in Turkey in 2007 and provided information that was used to build a cybercrime (link) case against Albert Gonzalez. After his arrest, Gonzalez tried to plea computer addiction and Asperger's disorder, which were dismissed by the court. Gonzalez is convicted to twenty years in prison
2009
The Israeli
invasion of Gaza originates a number of website defacements, denial-of-service attacks, and domain name and account hijackings, from both sides. These attacks are notable in being amongst the first ever politically motivated domain name hijackings.
During the Iranian election protests,
Anonymous plays a role in disseminating information to and from Iran by setting up the website Anonymous Iran and releasing a video manifesto to the Iranian government.
Janet Napolitano, DHS Secretary, opens new
National Cybersecurity and Communications Integration Center (NCCIC), a 24-hour "watch and warn" center.

The
Melbourne International Film Festival is forced to shut down its website after DDoS attacks by Chinese vigilantes, in response to Rebiya Kadeer's planned guest appearance, the screening of a film about her which is deemed "anti-China" by Chinese state media, and strong sentiments following the July 2009 Ürümqi riots. The hackers booked out all film sessions on its website, and replaced festival information with the Chinese flag and anti-Kadeer slogans.
Conficker worm infiltrates millions of PCs worldwide including many government-level top-security computer networks.
Computers of the
Climate Research Unit of East Anglia University are hacked in an attempt to expose a conspiracy by scientists to suppress data that contradicted their conclusions regarding global warming.
President Obama announces creation of a
Cyber-security Coordinator under the National Security Council and the National Economic Council responsible for implementing cybersecurity policies and strategy.
Spammers began using automatic translation services to send spam in other languages in order to overcome the fact that, by 2009, the majority of spam sent around the world was in the English language.
Sanford Wallace received a $711 million dollar judgment for spamming damages on Facebook, posting spam messages on member's walls. He files for bankruptcy.
A series of coordinated denial of service attacks against major government, news media, and financial websites in
South Korea and the United States are detected. While many think the attack is directed by North Korea, one researcher traces the attacks to the United Kingdom.
A 10-month cyberespionage investigation of the
GhostNet finds that 1,295 computers in 103 countries have been spied on, with circumstantial evidence pointing to China. GhostNet uses a malicious software program called gh0st RAT (remote-access tool) to steal sensitive documents and control webcams in infected computers.
Hackers break into Defense Department computers and download terabytes of data containing design information about the
Joint Strike Fighter project, a $300 billion initiative to develop a stealth fighter plane.
Previous Chapter –
Next Chapter: A New Cold War (Present)









































