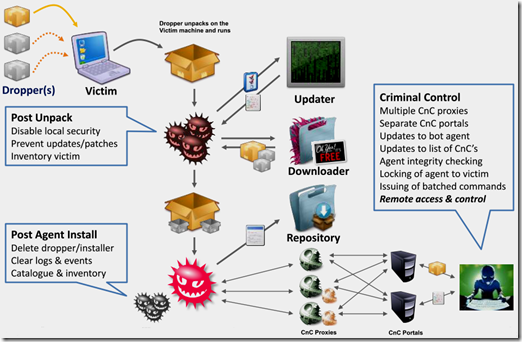
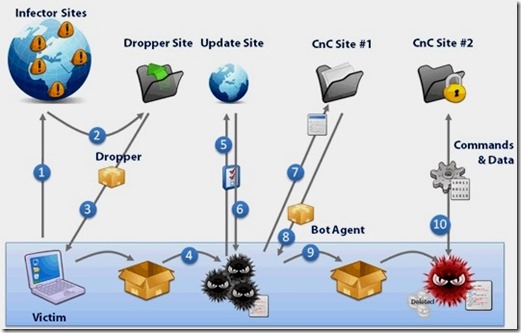
Cyber threats appear as quickly as new technologies themselves, and with computers now being such a critical part of our infrastructure – from our smartphones and cars to national energy systems and even prisons – the potential for damage is catastrophic. Large global multinationals and small local businesses and startups use the online infrastructure to facilitate economic and technological innovation. Defense and intelligence agencies depend on cyber networks to manage far-flung operations, analyze intelligence data and implement homeland security, military logistics and emergency services.
Global dependence on the Internet grows every day and many nations are now depending on a cyber infrastructure that enables the operation of financial markets, transportation networks, taxation and energy grids, as well as the public agencies protecting the health and security of their citizens. With this growth come ever-greater risks as well as opportunities.Advanced persistent threats reflect the risks posed by adversaries with the sophistication, resources and determination to cause real and permanent damage by exploiting the architecture of networks, and of cyberspace itself.
The biggest threat is state involvement. Where a rogue phisher or malware attack might be the criminal equivalent of a street mugger, state-sponsored attacks come with all the resources and technological sophistication of James Bond. Resistance is extremely hard and these attacks are very difficult to attribute to anyone; they can be routed via any country or written in any language.
Because the Internet is an evolving technology that carries enormous potential and vulnerabilities, cybersecurity problems implicate questions of Internet freedom, network architecture and the economic potential for cyberspace. We are at the beginning of a new and dangerous era of cyberwarfare and governments should be encouraged to cooperate in order to identify and punish the criminals. But let's not be naïve about it, they will also be engaging in cyber espionage against each other.
Cyberthreats for 2013
Cloud-Based Botnets
The trend to move the computer infrastructure to the cloud can not only jeopardize data, but can also be used to quickly create a “zombie army” – also known as botnet. Over the last years, Africa has become highly connected but many of the operating systems in use are pirated, meaning they are not receiving patches or updates. Therefore, Africa is a huge target for hackers and it is being used as a hub to target other countries – using command and control attacks, denial of service, phishing and spam.
The new undersea fiber optic cable along the east coast of Africa has enabled rapid growth in the number of users obtaining high speed connections to the internet creating a great opportunity for attackers to infect new machines and create new bots. A growing number of users in countries served by the cable had access to broadband links but without awareness about the need for computer protection, opening a new front for botnets.
Now, Africa is not attacking – they are being attacked and used. While businesses in Africa get some security, government and end users are totally exposed due to a of lack of awareness and money to invest in safe and legitimate software.
More Dangerous Malware
Malware creators will harden their software with techniques similar to those used in Digital Rights Management (DRM), which locks malware to infected systems. Malware attackers are also enhancing their abilities to compromise Mac operating systems and mobile devices, making their software cross platform and taking advantage of all the new smartphone features.
Search History Poisoning
Search engine poisoning is what happens when attackers manipulate a search engine’s algorithms to control the search results. Criminals often do this to get their own websites or clients’ websites on the first page of results. Search history may be the next step. With search history poisoning, criminals or politicians can manipulate a victim’s search history using cross-site request forgery.
Instead of compromising a computer, the attacker benefits because the manipulated history can become part of a user’s online profile so wherever that person goes online the forged history follows regardless of what device is used. The goal of this technique is to change what the victim reads online and is already being used by governments censoring what their citizens read.
Therefore, this can be a very powerful propaganda technique for politicians but also a super marketing idea for businesses trying to promote their products and services. This type of manipulation can also be used on social media sites, such as Facebook and Twitter, to falsely create an impression that there are many viewpoints to a certain post or that something is popular, when in reality, all boils down to one person is manipulating the algorithms.