After John Draper and his electronic whistling abilities gained a wide audience, there was a major shift in computing and hacking enjoyed a golden era of sorts in the 1980s. Society started becoming aware of hackers as computers became increasingly accessible and as networks grew in both size (number of terminals) and popularity (number of users) throughout the late seventies and early eighties.
During the 80s, the hacker population probably went up 1000-fold and there are mainly three events credited with doing the most in this area. Personal computer and clones were made available to the public at cheap prices. People could afford to buy a terminal and set up a BBS. And, where you find BBS's, you find hackers.
The movie War Games depicted the existence of hacking and the potential power associated with it. War Games displayed hacking as a glamorous thing and made it look easy. The movie shone a flashlight onto the hidden face of hacking, and introduced the wider public to the phenomenon. This created a degree of mass paranoia with the threat of hackers getting into any computer system and launching nuclear missiles. However, for a vast teenager audience, the movie gleaned a different message. It implied that hacking could get you girls. Cute girls…
Almost simultaneously, two novels had a great impact in popular culture: Cyberpunk, by Bruce Bethke, and Neuromancer, by William Gibson. The combination of the aforementioned factors catapulted hacker culture into the mainstream media.
By the late 1980s, the home PC had become more prevalent but large corporations still cornered the market on the technology. However, computers were no longer limited to the realms of hardcore hobbyists and business users; anyone, including existing and yet-to-be-realized hackers, could acquire a computer for their own purposes. Modems, enabling computers to communicate with each other over telephone lines, were also more widely available and significantly extended the hacker’s reach.
While phreakers were still blowing whistles into phone receivers, a new type of delinquent emerged; the cracker. This term, disputed until today, refers to a criminal hacker who uses his skills with criminal intentions far beyond the simple exploration of computer systems. This new breed of “hacker” directed its knowledge and tenacity toward distinctly criminal pursuits, including the distribution of pirated commercial software, games, and viruses and worms that could virtually shut down systems. Hacker and cracker clubs surged in popularity becoming nothing short of an epidemic, and in 1986, the U.S. government tried to thwart the problem by passing the Computer Fraud and Abuse Act (CFAA).
Historical Landmarks:
1980
Steve Bellovin, Tom Truscott and Jim Ellis develop and establish USENET for the UNIX to UNIX Copy (UUCP) architecture. USENET resembles a bulletin board system (BBS) but there is one major difference: the absence of a central server and dedicated administrator. USENET is a decentralized news network distributed among many servers that store and forward messages to one another.
1981
A group of German computer enthusiasts with a strong political orientation forms the Chaos Computer Club (CCC) in Hamburg.
Ian Murphy, along with three friends, hacks the server used by AT&T to meter people’s calls. He changes the internal clocks so that customers would get midnight discounts in the midday, while those who waited until midnight to call long distance were hit with high bills. For the incident, Murphy (known to his friends as Captain Zap) becomes the first hacker to be tried and convicted as a felon.

IBM introduces its first Personal Computer (PC) igniting a fast growth of the personal computer market. Its' a stand-alone machine, fully loaded with a 4.77 MHz Intel 8088 CPU and Microsoft´s MS-DOS operating system. Although the term personal computer is already in use alongside with "microcomputer" and "home computer", the IBM model 5150 sets the standard for what is later to be known as compatible PC products. Prior to this, the personal computer market is dominated by systems using the 6502 and Z80 8-bit microprocessors, such as the TRS 80 and Apple II series but from now on the standard will be the IBM PC compatible hardware platform.

1982
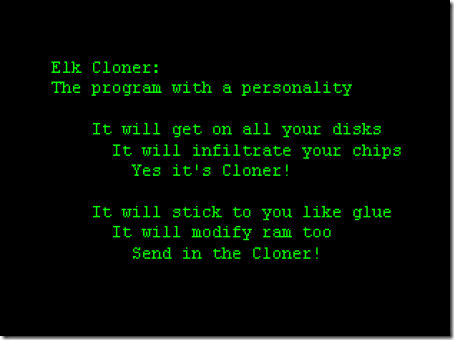
Rich Skrenta, a 15-year-old high school student, creates the Elk Cloner for the Apple II operative system. The Elk Cloner spreads using a technique now known as "boot sector" infection. If a computer boots from an infected floppy disk, a copy of the virus is loaded in the computer's memory. When an uninfected disk is inserted into the computer, the Elk Cloner copies itself to the disk, spreading from disk to disk.
In Manhattan, at the Memorial Sloan-Kettering Cancer Center, a system administrator for a DEC VAX 11/780 computer finds his system down. Soon, dozens of other systems around the country are reported as being hacked by the 414s, a group of Milwaukee teenagers aged 15 to 22 using their area code as name of the gang. Using home computers connected to ordinary telephone lines, the group breaks into 60 computer systems at institutions ranging from the Los Alamos Laboratories to hospitals and banks.
A KGB operative steals the plans for a sophisticated control system and its software from a Canadian firm. In order to prevent the use of this control system on the Trans-Siberian pipeline, the CIA inserts a piece of software code into the computers overseeing the pipeline that changes the workings of the system causing computational chaos. The effects of this logic bomb are a monumental explosion, showing the world the potential power of cyber warfare.
Scott Fahlman uses emoticons
:-) and :-(, with a specific suggestion that they be used to express emotion. 1983
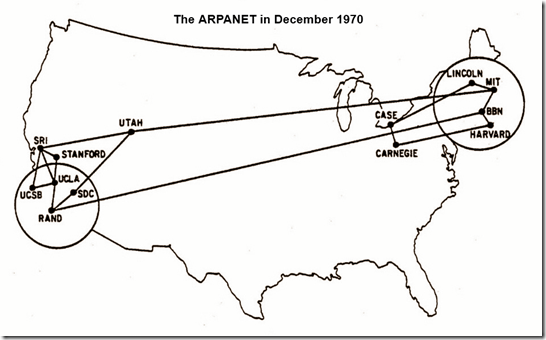
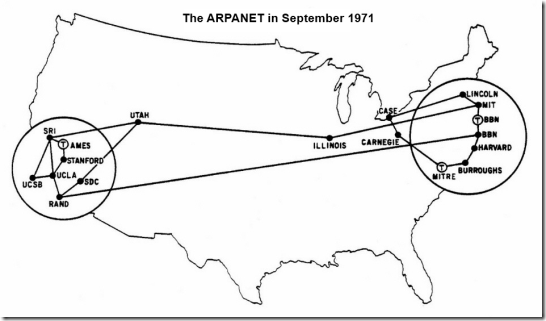
On January 1st, NCP is officially rendered obsolete and every machine connected to ARPANET has to use more flexible and powerful TCP/IP. This use of this new protocol suite marks the start of the modern Internet.
The University of Wisconsin creates the Domain Name System (DNS) allowing data packets to be directed to a domain name, which is translated by servers into the corresponding IP number.
Bruce Bethke publishes the short story Cyberpunk about information technology and cybernetics, mixed with a degree of radical change in the social order.

Ken Thompson describes a security exploit that he calls a "Trojan horse".
The FBI busts the "414s" and the incident appears as the cover story of Newsweek with the title "Beware: Hackers at play". As a result, the U.S. House of Representatives begins hearings on computer security hacking.
Fred Cohen coins the term "computer virus" to describe a computer program that can affect other computer programs by modifying them in such a way as to include a (possibly evolved) copy of itself.
The movie War Games popularizes hacking and introduces the general public to the phenomenon.

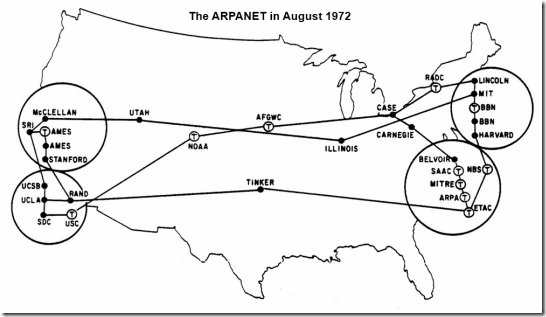
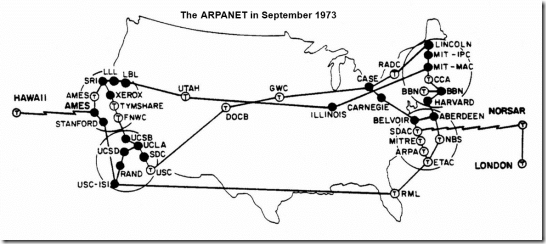
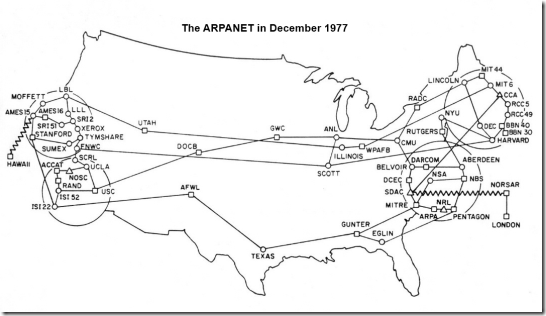
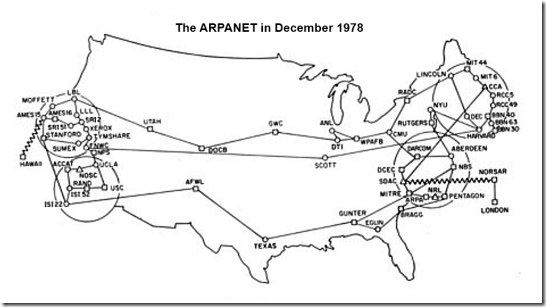
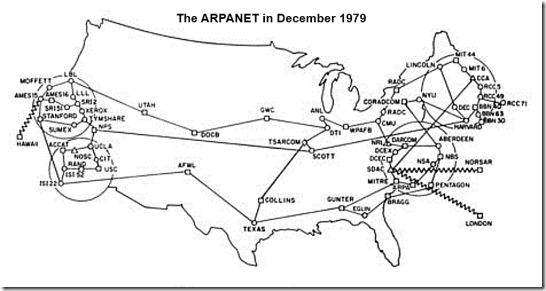
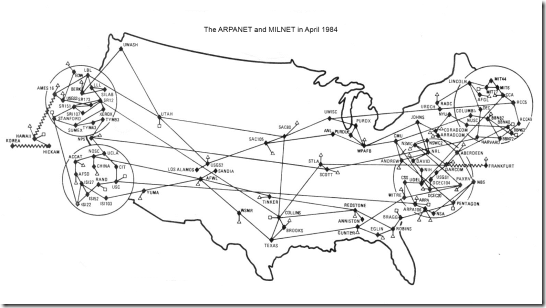
ARPANET splits into two separate networks: the Military Network (MILNET) for unclassified defense department communications and the ARPANET for the academic research community. Separating the civil and military networks reduces the 113-node ARPANET by 68 nodes.
1984
A mysterious character calling himself Lex Luthor founds the Legion of Doom (LoD), an elite group of hackers and phreakers committed to widely distribute their knowledge. Soon after, the Legion of Doom Technical Journal begins to show up on boards throughout the underground. The group includes some hackers that would soon enter history as a result of theirs actions, namely Erik Bloodaxe (Chris Goggans), The Mentor (Loyd Blankenship) and Phiber Optik (Mark Abene).
The Chaos Computer Club demonstrates a serious problem in the Bundespost‘s (German post office) new Bilschirmtext (BTX) interactive videotext service. Using the security flaws, the CCC transfers a sizable amount of money into their own bank account through a script that ran overnight as a demonstration to the press and returns the money publicly.
The first Chaos Communication Congress, the annual European hacker conference organized by the Chaos Computer Club, is held in Hamburg.
The US Comprehensive Crime Control Act gives Secret Service jurisdiction over computer fraud.
The hacker group Cult of the Dead Cow (cDc) forms in Lubbock, Texas and begins publishing its electronic magazine.

Eric Corley starts the hacker magazine 2600: The Hacker Quarterly exactly when TAP is putting out its final issue. The publication provides tips for would-be hackers and phone phreaks, as well as commentary on the hacker issues of the day along with a stream of explanations of how to exploit specific vulnerabilities in a wide range of operating systems and application environments.

William Gibson publishes Neuromancer, the first major cyberpunk novel. In it he coins the term “cyberspace”, term used to describe the network of computers through which his characters travel.

1985
Microsoft Windows 1.0 is released.

Phrack, an electronic magazine written by and for hackers, begins publishing. The uncensored commentary provides a fascinating glimpse over the personalities and world views of its contributors and editors.

Peter Sommer publishes The Hacker's Handbook.
In a joint operation involving several law enforcement agencies, a number of equipment from BBS operators and users alike is seized across New Jersey in an operation on the Private Sector BBS - the official bulletin board of 2600 magazine.
1986
Two Pakistani brothers, Basit Farooq Alvi and Amjad Farooq Alvi, write a computer program to protect their medical software from piracy, and it is supposed to target copyright infringers only. Brain affects the IBM PC computer by replacing the boot sector of a floppy disk with a copy of the virus. The virus changes the disk label to ©Brain and slows down the floppy disk drive. The program includes the brothers' address, three phone numbers, and a message that tells the user his machine is infected and to call them for inoculation. It is considered to be the first computer virus for MS-DOS.
Loyd Blankenship, the hacker member of LOD known as The Mentor is arrested. While in prison he writes The Hacker's Manifesto. Published in Phrak magazine, it soon becomes a true cornerstone of hacker culture.
Markus Hess, a German citizen recruited by the KGB, spies U.S. military information for the Soviets. Hess's hacking activities are discovered by Clifford Stoll, an astronomer working as systems administrator of the computer center of the Lawrence Berkeley Laboratory (LBL) in California. Hess was able to attack 400 U.S. military computers by using LBL to get into ARPANET and MILNET before being stopped.
The Internet Engineering Task Force or IETF is created to serve as a forum for technical coordination by contractors for DARPA working on ARPANET, US Defense Data Network, and the Internet core gateway system.

Seventeen year old Herbert Zinn is arrested after hacking into U.S. military and AT&T computers for months.
1987
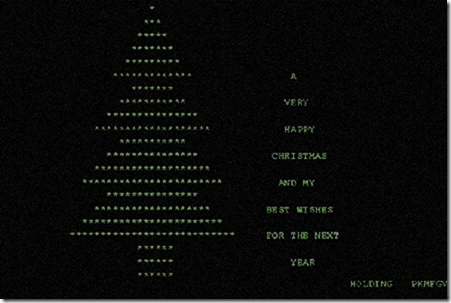
A student at the Clausthal University of Technology, using the REXX scripting language, writes the Christmas Tree EXEC worm and causes major disruption to the European Academic Research Network, the BITNET, and IBM's worldwide VNET networks. The program draws a crude Christmas tree as text graphics, then sends itself to each entry in the target's email contacts file. It is the first widely disruptive computer worm.
1988
The First National Bank of Chicago is the victim of $70-million computer theft.
Robert Tappan Morris, a graduate student at Cornell University, allegedly plans to perform an experiment to map the size of the ARPANET. To attain this goal, he writes a program capable of copying itself across the network but after 12 hours of its release, the worm is completely out of control and is has infected already at least 6,000 UNIX servers, approximately 10% of entire network, clogging government and university systems. It will take years completely eradicate the worm causing damages estimated at around $10,000,000. Morris is dismissed from Cornell, sentenced to three years' probation, and fined $10K.

Is response to the Morris worm incident, the Computer Emergency Response Team (CERT) is founded.
The Father Christmas worm spreads over DECnet networks attacking VAX/VMS systems with the aim of sending a Christmas greeting from "Father Christmas" to the affected system.
Dave Rhodes, a college student who wanted to make a little extra cash with little extra effort, creates the first known electronic chain letter, titled Make Money Fast.
Jarkko Oikarinen creates the first Internet chat network, called Internet Relay Chat (IRC).
The Jerusalem virus causes a major epidemic being detected in many enterprises, government offices and academic institutions on Friday, May 13th. It duplicates itself every Friday and on the 13th of the month, causing system slowdown; however, on every Friday the 13th after May 13, 1988, it also corrupts all available disks on the infected systems.
1989
The Datacrime virus (a Jerusalem modification) appears and is extremely dangerous: from October 13th through December 31st, it initiates a low-level formatting of a hard disc's zero cylinder which leads to the destruction of tables stored in FAT files and irrevocable loss of data.
Acid Phreak (Eli Ladopoulos) founds the Masters of Deception (MOD), a new hacker group based in New York. After a series of disputes, Phiber Optik and Erik Bloodaxe leave the LOD and join the MOD.
A group of German hackers led by Karl Koch, who was loosely affiliated with the CCC, is arrested for acts of cyber espionage like breaking into US government and corporate computers and selling operating-system source code to the KGB. Markus Hess, discovered by Clifford Stoll, is part of this group.
The 24th issue of Phrack includes an administrative document, copied from a BellSouth computer, describing the organization of the Enhanced 911 emergency response system.
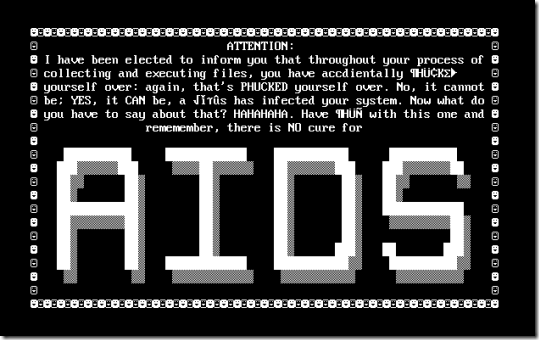
Joseph Popp unleashes the first large-scale computer extortion scheme. 20,000 discs containing a trojan are sent to addresses all over the world. Under the pretense of a quiz on the AIDS virus, users unwittingly load the program that would automatically installs itself on the system, creating its own concealed files and directories and modifying system files. After 90 loads, the operating system encoded the names of all files, rendering them invisible and leaving only one file accessible. This file threatens to destroy all computer data unless the user pays $500 into a foreign account.
The politically motivated WANK worm spreads over DECnet. VMS machines worldwide are penetrated by the anti-nuclear worm having their login screens altered to:

The WANK worm is the first documented case of hacktivism.
Tim Berners-Lee proposes an information management system using the Hypertext Transfer Protocol (HTTP). It’s the birth of the World Wide Web.
Kevin Mitnick secretly monitors the e-mail of MCI and DEC security officials. He is convicted of damaging computers and stealing software and sentenced to a year in jail.

Kevin Poulsen (Dark Dante) is indicted on 19 counts of conspiracy, fraud, wiretapping and money laundering. He goes on the run and avoids capture for 17 months.

Previous Chapter – Next Chapter: The Internet Expansion (1990s)