35 Facebook false websites
Security Web-Center found 35 Facebook phishing websites. These spammers create fake pages that look like the Facebook login page. If you enter your email and password on one of these pages, the spammer records your information and keeps it. The fake sites, like the one below, use a similar URL to Facebook.com in an attempt to steal people's login information.
The people behind these websites, then use the information to access victims' accounts and send messages to their friends, further propagating the illegitimate sites. In some instances, the phishers make money by exploiting the personal information they've obtained. Check out the list:
Graphene bubbles improve lithium-air batteries
A team of scientists from the Pacific Northwest National Laboratory and Princeton University used a new approach to buil a graphene membrane for use in lithium-air batteries, which could, one day, replace conventional batteries in electric vehicles. Resembling coral, this porous graphene material could replace the traditional smooth graphene sheets in lithium-air batteries, which become clogged with tiny particles during use.
Resembling broken eggshells, graphene structures built around bubbles produced a lithium-air battery with the highest energy capacity to date. As an added bonus, the team’s new material does not rely on platinum or other precious metals, reducing its potential cost and environmental impact.
New botnets arrive
The recent breakup of the ChangeDNS botnet which infected more than 4 million computers and was under the control of a single ring of criminals raised a new set of concerns. The biggest effect of the commoditization of botnet tools and other computer security exploits might be a new wave of major botnet attacks, driven by people who simply buy their malware from the equivalent of an app store—or who rent it as a service.
The botnet market is nothing new—it's been evolving for years. But what is new is the business model of botnet developers, which has matured to the point where it begins to resemble other, legitimate software markets. One example of this change is a Facebook and Twitter CAPTCHA bypass bot called JET, which is openly for sale online.
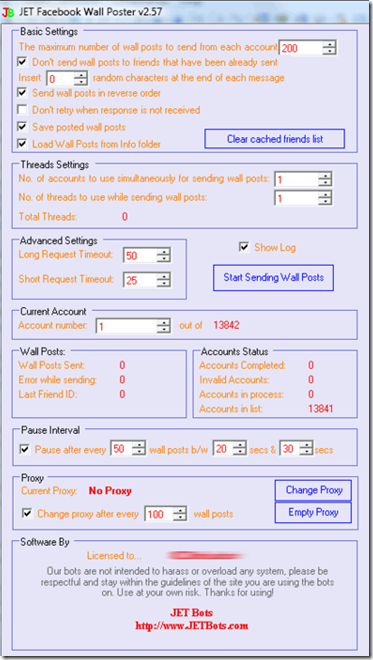 |
| The JET Facebook posting bot from jetbots.com |
Tor Project turns to Amazon
The Tor Project offers a channel for people wanting to route their online communications anonymously and this channel has been used by activists to avoid censorship as well as those seeking anonymity for more nefarious reasons. Now the people involved in this project to maintain a secret layer of the internet have turned to Amazon to add bandwidth to the service. According to some experts, the use of Amazon's cloud service will make it harder for governments to track.
Amazon's cloud service - dubbed EC2 (Elastic Compute Cloud) offers virtual computer capacity. The Tor developers are calling on people to sign up to the service in order to run a bridge - a vital point of the secret network through which communications are routed. According to Tor developers, by setting up a bridge, you donate bandwidth to the Tor network and help improve the safety and speed at which users can access the internet.
World’s lightest material
Ultra light (<10 milligrams per cubic centimeter) cellular materials are desirable for thermal insulation, battery electrodes, catalyst supports, and acoustic, vibration, or shock energy damping. A team of researchers from UC Irvine, HRL Laboratories and the California Institute of Technology have developed the world's lightest material – with a density of 0.9 mg/cc. The new material redefines the limits of lightweight materials because of its unique "micro-lattice" cellular architecture. The researchers were able to make a material that consists of 99.99 percent air by designing the 0.01 percent solid at the nanometer, micron and millimeter scales. "The trick is to fabricate a lattice of interconnected hollow tubes with a wall thickness 1,000 times thinner than a human hair," said lead author Dr. Tobias Schaedler of HRL.
 |
| Photo by Dan Little, HDR Laboratories |
The material's architecture allows unprecedented mechanical behavior for a metal, including complete recovery from compression exceeding 50 percent strain and extraordinarily high energy absorption. "Materials actually get stronger as the dimensions are reduced to the nanoscale," explained UCI mechanical and aerospace engineer Lorenzo Valdevit, UCI's principal investigator on the project. "Combine this with the possibility of tailoring the architecture of the micro-lattice and you have a unique cellular material."
William Carter, manager of the architected materials group at HRL, compared the new material to larger, more familiar edifices: "Modern buildings, exemplified by the Eiffel Tower or the Golden Gate Bridge, are incredibly light and weight-efficient by virtue of their architecture. We are revolutionizing lightweight materials by bringing this concept to the nano and micro scales."
Adapted from PhysOrg
Butterfly wings inspire new design
Engineers have been trying to create water repellent surfaces, but past attempts at artificial air traps tended to lose their contents over time due to external perturbations. Now an international team of researchers from Sweden, the United States, and Korea has taken advantage of what might normally be considered defects in the nanomanufacturing process to create a multilayered silicon structure that traps air and holds it for longer than one year.

Researchers mimicked the many-layered nanostructure of blue mountain swallowtail (Papilio ulysses) wings to make a silicon wafer that traps both air and light. The brilliant blue wings of this butterfly easily shed water because of the way ultra-tiny structures in the wings trap air and create a cushion between water and wing.

The researchers used an etching process to carve out micro-scale pores and sculpt tiny cones from the silicon. The team found that features of the resulting structure that might usually be considered defects, such as undercuts beneath the etching mask and scalloped surfaces, actually improved the water repellent properties of the silicon by creating a multilayered hierarchy of air traps. The intricate structure of pores, cones, bumps, and grooves also succeeded in trapping light, almost perfectly absorbing wavelengths just above the visible range.
US military ready for cyber warfare
The US military is now legally in the clear to launch offensive operations in cyberspace, the commander of the US Strategic Command said Wednesday, less than a month after terming this a work in progress.
Air Force General Robert Kehler said in the latest sign of quickening U.S. military preparations for possible cyber warfare that "I do not believe that we need new explicit authorities to conduct offensive operations of any kind". "I do not think there is any issue about authority to conduct operations," he added, referring to the legal framework.

But he said the military was still working its way through cyber warfare rules of engagement that lie beyond "area of hostilities," or battle zones, for which they have been approved.
The US Strategic Command is in charge of a number of areas for the US military, including space operations (like military satellites), cyberspace concerns, 'strategic deterrence' and combating WMDs. The U.S. Cyber Command, a sub-command, began operating in May 2010 as military doctrine, legal authorities and rules of engagement were still being worked out for what the military calls the newest potential battle "domain."
"When warranted, we will respond to hostile acts in cyberspace as we would to any other threat to our country," the DoD said in the report. "All states possess an inherent right to self-defense, and we reserve the right to use all necessary means – diplomatic, informational, military, and economic – to defend our nation, our allies, our partners, and our interests."
The Office of the National Counterintelligence Executive, a U.S. intelligence arm, said in a report to Congress last month that China and Russia are using cyber espionage to steal U.S. trade and technology secrets and that they will remain "aggressive" in these efforts.
It defined cyberspace as including the Internet, telecommunications networks, computer systems and embedded processors and controllers in "critical industries."

The Pentagon, in the report to Congress made public Tuesday, said it was seeking to deter aggression in cyberspace by building stronger defenses and by finding ways to make attackers pay a price.
Windows 8 first malware bootkit
An independent programmer and security analyst, Peter Kleissner, is planning to release the world's first Windows 8 bootkit in India, at the International Malware Conference (MalCon).
A bootkit is a rootkit that is able to load from a master boot record and persist in memory all the way through the transition to protected mode and the startup of the OS. It’s a boot virus that is able to hook and patch Windows to get load into the Windows kernel, and thus getting unrestricted access to the entire computer. It is even able to bypass full volume encryption, because the master boot record (where Stoned is stored) is not encrypted. The master boot record contains the decryption software which asks for a password and decrypts the drive. This is the weak point, the master boot record, which will be used to take over the whole system.
A bootkit is built upon the following broad parts:
- Infector
- Bootkit
- Drivers
- Plugins (the payload)
A bootkit is a rootkit that is able to load from a master boot record and persist in memory all the way through the transition to protected mode and the startup of the OS. It’s a boot virus that is able to hook and patch Windows to get load into the Windows kernel, and thus getting unrestricted access to the entire computer. It is even able to bypass full volume encryption, because the master boot record (where Stoned is stored) is not encrypted. The master boot record contains the decryption software which asks for a password and decrypts the drive. This is the weak point, the master boot record, which will be used to take over the whole system.
Stuxnet 3.0 released at MalCon?
Security researchers were shocked to see in a twitter update from MalCon that one of the research paper submissions shortlisted is on possible features of Stuxnet 3.0. While this may just be a discussion and not a release, it is interesting to note that the speaker Nima Bagheri presenting the paper is from IRAN.
The research paper abstract discusses rootkit features and the malware authors may likely show demonstration at MalCon with new research related to hiding rootkits and advanced Stuxnet like malwares.
Stuxnet is a computer worm discovered in June 2010. It targets Siemens industrial software and equipment running Microsoft Windows. While it is not the first time that hackers have targeted industrial systems, it is the first discovered malware that spies on and subverts industrial systems, and the first to include a programmable logic controller (PLC) rootkit.
What is alarming is the recent discovery (On 1 September 2011) by The Laboratory of Cryptography and System Security (CrySyS) of the Budapest University of Technology and Economics, of a new worm theoretically related to Stuxnet. After analyzing the malware, they named it Duqu and Symantec, based on this report, continued the analysis of the threat, calling it "nearly identical to Stuxnet, but with a completely different purpose", and published a detailed technical paper. The main component used in Duqu is designed to capture information such as keystrokes and system information and this data may be used to enable a future Stuxnet-like attack.
New biosensor made of nanotubes
Standard sensors employ metal electrodes coated with enzymes that react with compounds and produce an electrical signal that can be measured. However,the inefficiency of those sensors leads to imperfect measurements. Now, scientists at Purdue University have developed a new method for stacking synthetic DNA and carbon nanotubes onto a biosensor electrode.
Carbon nanotubes, cylindrically shaped carbon molecules known to have excellent thermal and electrical properties, have been seen as a possibility for improving sensor performance. The problem is that the materials are not fully compatible with water, which limits their application in biological fluids.
Marshall Porterfield and Jong Hyun Choi have found a solution and reported their findings in the journal The Analyst, describing a sensor that essentially builds itself.
"In the future, we will be able to create a DNA sequence that is complementary to the carbon nanotubes and is compatible with specific biosensor enzymes for the many different compounds we want to measure," Porterfield said. "It will be a self-assembling platform for biosensors at the biomolecular level."
Choi developed a synthetic DNA that will attach to the surface of the carbon nanotubes and make them more water-soluble. "Once the carbon nanotubes are in a solution, you only have to place the electrode into the solution and charge it. The carbon nanotubes will then coat the surface," Choi said.
The electrode coated with carbon nanotubes will attract the enzymes to finish the sensor's assembly. The sensor described in the findings was designed for glucose. But Porterfield said it could be easily adapted for various compounds. "You could mass produce these sensors for diabetes, for example, for insulin management for diabetic patients," Porterfield said.
Carbon nanotubes, cylindrically shaped carbon molecules known to have excellent thermal and electrical properties, have been seen as a possibility for improving sensor performance. The problem is that the materials are not fully compatible with water, which limits their application in biological fluids.
Marshall Porterfield and Jong Hyun Choi have found a solution and reported their findings in the journal The Analyst, describing a sensor that essentially builds itself.
"In the future, we will be able to create a DNA sequence that is complementary to the carbon nanotubes and is compatible with specific biosensor enzymes for the many different compounds we want to measure," Porterfield said. "It will be a self-assembling platform for biosensors at the biomolecular level."
Choi developed a synthetic DNA that will attach to the surface of the carbon nanotubes and make them more water-soluble. "Once the carbon nanotubes are in a solution, you only have to place the electrode into the solution and charge it. The carbon nanotubes will then coat the surface," Choi said.
The electrode coated with carbon nanotubes will attract the enzymes to finish the sensor's assembly. The sensor described in the findings was designed for glucose. But Porterfield said it could be easily adapted for various compounds. "You could mass produce these sensors for diabetes, for example, for insulin management for diabetic patients," Porterfield said.
Operation Brotherhood Takedown
Friday, the hacktivist collective known as Anonymous successfully disabled some prominent Egyptian Muslim Brotherhood website. Anonymous is targeting the Muslim Brotherhood in Egypt, claiming the Muslim Brotherhood is a threat to the Egyptian revolution.
Earlier in the week, the hacktivist group had made an announcement to launch a DDoS attack, “Operation Brotherhood Takedown,” on all Brotherhood sites at 8pm on Friday, 11 November and they delivered.
Anonymous announced Saturday that DDoS attacks on the Muslim Brotherhood would continue until November 18.
The Brotherhood claimed in a statement released on Saturday morning that the attacks were coming from Germany, France, Slovakia and San Francisco in the US, with 2000-6000 hits per second. The hackers later escalated their attack on the site to 380 thousand hits per second. Under the overload, four of the group’s websites were forced down temporarily.
Earlier in the week, the hacktivist group had made an announcement to launch a DDoS attack, “Operation Brotherhood Takedown,” on all Brotherhood sites at 8pm on Friday, 11 November and they delivered.
Anonymous announced Saturday that DDoS attacks on the Muslim Brotherhood would continue until November 18.
The Brotherhood claimed in a statement released on Saturday morning that the attacks were coming from Germany, France, Slovakia and San Francisco in the US, with 2000-6000 hits per second. The hackers later escalated their attack on the site to 380 thousand hits per second. Under the overload, four of the group’s websites were forced down temporarily.
FBI's Operation Ghost Click
Resulting from a two-year investigation by the FBI, dubbed "Operation Ghost Click", a gang of internet bandits who stole $14 million after hacking into at least 4 million computers in an online advertising scam have been arrested.
Six Estonian nationals have been arrested and charged with running a sophisticated Internet fraud ring that infected millions of computers worldwide with a virus and enabled the thieves to manipulate the multi-billion-dollar Internet advertising industry. Users of infected machines were unaware that their computers had been compromised—or that the malicious software rendered their machines vulnerable to a host of other viruses.
Computers in more than 100 countries were infected by the “DNSChanger” malware, which redirected searches for Apple’s iTunes store to fake pages pretending to offer Apple software for sale, as well as sending those searching for information on the U.S. Internal Revenue Service to accounting company H&R Block, which allegedly paid those behind the scam a fee for each visitor via a fake internet ad agency. Beginning in 2007, the cyber ring used DNSChanger to infect approximately 4 million computers in more than 100 countries.
Trend Micro, which helped supply information to the FBI on DNS Changer, hailed the law enforcement operation as the "biggest cyber criminal takedown in history." Whilst the rogue DNS servers have been replaced, many may still be infected. Head here to learn about how to check if your system is part of the DNS Changer botnet.
Six Estonian nationals have been arrested and charged with running a sophisticated Internet fraud ring that infected millions of computers worldwide with a virus and enabled the thieves to manipulate the multi-billion-dollar Internet advertising industry. Users of infected machines were unaware that their computers had been compromised—or that the malicious software rendered their machines vulnerable to a host of other viruses.
Computers in more than 100 countries were infected by the “DNSChanger” malware, which redirected searches for Apple’s iTunes store to fake pages pretending to offer Apple software for sale, as well as sending those searching for information on the U.S. Internal Revenue Service to accounting company H&R Block, which allegedly paid those behind the scam a fee for each visitor via a fake internet ad agency. Beginning in 2007, the cyber ring used DNSChanger to infect approximately 4 million computers in more than 100 countries.
Trend Micro, which helped supply information to the FBI on DNS Changer, hailed the law enforcement operation as the "biggest cyber criminal takedown in history." Whilst the rogue DNS servers have been replaced, many may still be infected. Head here to learn about how to check if your system is part of the DNS Changer botnet.
Electron Tweezers
A recent paper by researchers from the National Institute of Standards and Technology (NIST) and the University of Virginia (UVA) demonstrates that the beams produced by modern electron microscopes can be used to manipulate nanoscale objects.
The tool is an electron version of the laser "optical tweezers" that have become a standard tool in biology, physics and chemistry for manipulating tiny particles. Except that electron beams could offer a thousand-fold improvement in sensitivity and resolution.
If you just consider the physics, you might expect that a beam of focused electrons -- such as that created by a transmission electron microscope (TEM) -- could do the same thing. However that's never been seen, in part because electrons are much fussier to work with. They can't penetrate far through air, for example, so electron microscopes use vacuum chambers to hold specimens.
So Vladimir Oleshko and his colleague James Howe, were surprised when, in the course of another experiment, they found themselves watching an electron tweezer at work. They were using an electron microscope to study, in detail, what happens when a metal alloy melts or freezes. They were observing a small particle -- a few hundred microns wide -- of an aluminum-silicon alloy held just at a transition point where it was partially molten, a liquid shell surrounding a core of still solid metal.
"This effect of electron tweezers was unexpected because the general purpose of this experiment was to study melting and crystallization," Oleshko explains. "We can generate this sphere inside the liquid shell easily; you can tell from the image that it's still crystalline. But we saw that when we move or tilt the beam -- or move the microscope stage under the beam -- the solid particle follows it, like it was glued to the beam."
Potentially, electron tweezers could be a versatile and valuable tool, adding very fine manipulation to wide and growing lists of uses for electron microscopy in materials science. "Of course, this is challenging because it requires a vacuum," he says, "but electron probes can be very fine, three orders of magnitude smaller than photon beams -- close to the size of single atoms. We could manipulate very small quantities, even single atoms, in a very precise way."
(Adapted from ScienceDaily)
The tool is an electron version of the laser "optical tweezers" that have become a standard tool in biology, physics and chemistry for manipulating tiny particles. Except that electron beams could offer a thousand-fold improvement in sensitivity and resolution.
If you just consider the physics, you might expect that a beam of focused electrons -- such as that created by a transmission electron microscope (TEM) -- could do the same thing. However that's never been seen, in part because electrons are much fussier to work with. They can't penetrate far through air, for example, so electron microscopes use vacuum chambers to hold specimens.
So Vladimir Oleshko and his colleague James Howe, were surprised when, in the course of another experiment, they found themselves watching an electron tweezer at work. They were using an electron microscope to study, in detail, what happens when a metal alloy melts or freezes. They were observing a small particle -- a few hundred microns wide -- of an aluminum-silicon alloy held just at a transition point where it was partially molten, a liquid shell surrounding a core of still solid metal.
"This effect of electron tweezers was unexpected because the general purpose of this experiment was to study melting and crystallization," Oleshko explains. "We can generate this sphere inside the liquid shell easily; you can tell from the image that it's still crystalline. But we saw that when we move or tilt the beam -- or move the microscope stage under the beam -- the solid particle follows it, like it was glued to the beam."
Potentially, electron tweezers could be a versatile and valuable tool, adding very fine manipulation to wide and growing lists of uses for electron microscopy in materials science. "Of course, this is challenging because it requires a vacuum," he says, "but electron probes can be very fine, three orders of magnitude smaller than photon beams -- close to the size of single atoms. We could manipulate very small quantities, even single atoms, in a very precise way."
(Adapted from ScienceDaily)
Memory at the nanoscale
Metallic alloys can be stretched or compressed in such a way that they stay deformed once the strain on the material has been released. However, shape memory alloys can return to their original shape after being heated above a specific temperature.
Now, for the first time, two physicists from the University of Constance determined the absolute values of temperatures at which shape memory nanospheres start changing back to their memorized shape, undergoing the so-called structural phase transition, which depends on the size of particles studied. To achieve this result, they performed a computer simulation using nanoparticles with diameters between 4 and 17 nm made of an alloy of equal proportions of nickel and titanium.
To date, research efforts to establish structural phase transition temperature have mainly been experimental. Most of the prior work on shape memory materials was in macroscopic scale systems and used for applications such as dental braces, stents or oil temperature-regulating devices for bullet trains.
Thanks to a computerized method known as molecular dynamics simulation, Daniel Mutter and Peter Nielaba were able to visualize the transformation process of the material during the transition. As the temperature increased, they showed that the material's atomic-scale crystal structure shifted from a lower to a higher level of symmetry. They found that the strong influence of the energy difference between the low- and high-symmetry structure at the surface of the nanoparticle, which differed from that in its interior, could explain the transition.
Potential new applications include the creation of nanoswitches, where laser irradiation could heat up such shape memory material, triggering a change in its length that would, in turn, function as a switch.
Now, for the first time, two physicists from the University of Constance determined the absolute values of temperatures at which shape memory nanospheres start changing back to their memorized shape, undergoing the so-called structural phase transition, which depends on the size of particles studied. To achieve this result, they performed a computer simulation using nanoparticles with diameters between 4 and 17 nm made of an alloy of equal proportions of nickel and titanium.
To date, research efforts to establish structural phase transition temperature have mainly been experimental. Most of the prior work on shape memory materials was in macroscopic scale systems and used for applications such as dental braces, stents or oil temperature-regulating devices for bullet trains.
Thanks to a computerized method known as molecular dynamics simulation, Daniel Mutter and Peter Nielaba were able to visualize the transformation process of the material during the transition. As the temperature increased, they showed that the material's atomic-scale crystal structure shifted from a lower to a higher level of symmetry. They found that the strong influence of the energy difference between the low- and high-symmetry structure at the surface of the nanoparticle, which differed from that in its interior, could explain the transition.
Potential new applications include the creation of nanoswitches, where laser irradiation could heat up such shape memory material, triggering a change in its length that would, in turn, function as a switch.
Operation Muslim Brotherhood
Anonymous targets Muslim Brotherhood in Egypt claiming this organization is a threat to the Egyptian revolution and plans a coordinated Distributed Denial of Service attack on Nov. 11.
Monday, those claiming to represent the international hacktivist collective released a YouTube video announcing an operation directed at the Muslim Brotherhood. According to the announcement, the Muslim Brotherhood is a “corrupt” organization “bent on taking over sovereign Arab states in its quest to seize power.” The announcement goes on to compare the Muslim Brotherhood to the Church of Scientology, and declares the Brotherhood to be “a threat to the people.”
Monday, those claiming to represent the international hacktivist collective released a YouTube video announcing an operation directed at the Muslim Brotherhood. According to the announcement, the Muslim Brotherhood is a “corrupt” organization “bent on taking over sovereign Arab states in its quest to seize power.” The announcement goes on to compare the Muslim Brotherhood to the Church of Scientology, and declares the Brotherhood to be “a threat to the people.”
Like any announcement from those claiming to represent Anonymous, there are no guarantees. The ultimate success or failure of any Anonymous operation is determined by the hive mind. Whether or not Anonymous manages to launch a successful operation against the Muslim Brotherhood remains to be seen.
Quantum Cloning Advances
Quantum cloning is the process that takes an arbitrary, unknown quantum state and makes an exact copy without altering the original state in any way. Quantum cloning is forbidden by the laws of quantum mechanics as shown by the no cloning theorem. Though perfect quantum cloning is not possible, it is possible to perform imperfect cloning, where the copies have a non-unit fidelity with the state being cloned.
The quantum cloning operation is the best way to make copies of quantum information therefore cloning is an important task in quantum information processing, especially in the context of quantum cryptography. Researchers are seeking ways to build quantum cloning machines, which work at the so called quantum limit. Quantum cloning is difficult because quantum mechanics laws only allow for an approximate copy—not an exact copy—of an original quantum state to be made, as measuring such a state prior to its cloning would alter it. The first cloning machine relied on stimulated emission to copy quantum information encoded into single photons.
Scientists in China have now produced a theory for a quantum cloning machine able to produce several copies of the state of a particle at atomic or sub-atomic scale, or quantum state. A team from Henan Universities in China, in collaboration with another team at the Institute of Physics of the Chinese Academy of Sciences, have produced a theory for a quantum cloning machine able to produce several copies of the state of a particle at atomic or sub-atomic scale, or quantum state. The advance could have implications for quantum information processing methods used, for example, in message encryption systems.
In this study, researchers have demonstrated that it is theoretically possible to create four approximate copies of an initial quantum state, in a process called asymmetric cloning. The authors have extended previous work that was limited to quantum cloning providing only two or three copies of the original state. One key challenge was that the quality of the approximate copy decreases as the number of copies increases.
The authors were able to optimize the quality of the cloned copies, thus yielding four good approximations of the initial quantum state. They have also demonstrated that their quantum cloning machine has the advantage of being universal and therefore is able to work with any quantum state, ranging from a photon to an atom. Asymmetric quantum cloning has applications in analyzing the security of messages encryption systems, based on shared secret quantum keys.
The quantum cloning operation is the best way to make copies of quantum information therefore cloning is an important task in quantum information processing, especially in the context of quantum cryptography. Researchers are seeking ways to build quantum cloning machines, which work at the so called quantum limit. Quantum cloning is difficult because quantum mechanics laws only allow for an approximate copy—not an exact copy—of an original quantum state to be made, as measuring such a state prior to its cloning would alter it. The first cloning machine relied on stimulated emission to copy quantum information encoded into single photons.
Scientists in China have now produced a theory for a quantum cloning machine able to produce several copies of the state of a particle at atomic or sub-atomic scale, or quantum state. A team from Henan Universities in China, in collaboration with another team at the Institute of Physics of the Chinese Academy of Sciences, have produced a theory for a quantum cloning machine able to produce several copies of the state of a particle at atomic or sub-atomic scale, or quantum state. The advance could have implications for quantum information processing methods used, for example, in message encryption systems.
In this study, researchers have demonstrated that it is theoretically possible to create four approximate copies of an initial quantum state, in a process called asymmetric cloning. The authors have extended previous work that was limited to quantum cloning providing only two or three copies of the original state. One key challenge was that the quality of the approximate copy decreases as the number of copies increases.
The authors were able to optimize the quality of the cloned copies, thus yielding four good approximations of the initial quantum state. They have also demonstrated that their quantum cloning machine has the advantage of being universal and therefore is able to work with any quantum state, ranging from a photon to an atom. Asymmetric quantum cloning has applications in analyzing the security of messages encryption systems, based on shared secret quantum keys.
Anonymous continues #OpDarkNet
Anonymous exposes 190 Internet pedophiles as part of the still ongoing Operation DarkNet.
Early this week, those claiming to represent the hacktivist collective known as Anonymous released the IP addresses of 190 alleged Internet pedophiles. According to them, the group planned and successfully executed a complex social engineering operation dubbed “Paw Printing.”
By tricking kiddie porn enthusiasts into downloading a phony security upgrade, the hacktivists were able to track and record the IP addresses of pedophiles visiting known child pornography sites like Lolita City and Hard Candy, hosted somewhere in the creepy world of the DarkNet.
The DarkNet is a mysterious and deliberately hidden part of the Internet where criminals, and others in need of anonymity and privacy mingle. Within the hidden world of this so called Invisible Web one might engage in myriad activities, legal and otherwise. On the DarkNet one might buy or sell drugs, obtain or sell fake IDs, sponsor terrorism, rent a botnet or trade in kiddie porn.
In their announcement Anonymous gives a detailed account of their month long child pornography sting which culminated in late October when, over a 24 hour period, Anonymous collected the 190 IP addresses associated with the alleged Internet pedophiles.
The hacktivists claim they are not out to destroy the DarkNet, only to expose pedophiles who use the anonymity and clandestine nature of that hidden part of the Web to exploit innocent children for perverse sexual gratification.
Early this week, those claiming to represent the hacktivist collective known as Anonymous released the IP addresses of 190 alleged Internet pedophiles. According to them, the group planned and successfully executed a complex social engineering operation dubbed “Paw Printing.”
By tricking kiddie porn enthusiasts into downloading a phony security upgrade, the hacktivists were able to track and record the IP addresses of pedophiles visiting known child pornography sites like Lolita City and Hard Candy, hosted somewhere in the creepy world of the DarkNet.
The DarkNet is a mysterious and deliberately hidden part of the Internet where criminals, and others in need of anonymity and privacy mingle. Within the hidden world of this so called Invisible Web one might engage in myriad activities, legal and otherwise. On the DarkNet one might buy or sell drugs, obtain or sell fake IDs, sponsor terrorism, rent a botnet or trade in kiddie porn.
In their announcement Anonymous gives a detailed account of their month long child pornography sting which culminated in late October when, over a 24 hour period, Anonymous collected the 190 IP addresses associated with the alleged Internet pedophiles.
 |
| Anonymous executes Pedobear (the internet meme for pedophiles) |
The hacktivists claim they are not out to destroy the DarkNet, only to expose pedophiles who use the anonymity and clandestine nature of that hidden part of the Web to exploit innocent children for perverse sexual gratification.
Subscribe to:
Posts (Atom)








