The Low Orbit Ion Cannon, or LOIC, is a popular tool for taking down websites these days. It was used on Visa, Master Card, Paypal and other institutions by "Anonymous" hacktivists.
A new weapon of mass awareness is in the horizon, however, that may very well step up the severity and efficiency of these attacks. If effective, it will set into motion attacks originating from thousands of computers worldwide. The difference? End-users will not necessarily know they are participating in the attacks.
Thought BitTorrent was just about downloading movies and TV shows? Think again: The BitTorrent protocol can be abused to initiate massive denial of service attacks, which could be used to take down large-scale websites. This exploit is based on BitTorrent’s ability to download data without the help of any centralized server, also known as trackerless BitTorrent. Here's how it would work.
A home user navigates to a torrent search engine to download a popular file (a film or TV show, for instance).The file may have several thousands of leechers or seeders; these numbers may increase to the hundreds of thousands in some cases, depending on the popularity of the file. For simplicity, think of each leecher as one computer attempting to download the file.
BitTorrent was originally designed with a central server dubbed tracker in mind which would help users interested in the same file find each other to facilitate downloads. However, these tracker servers have become a kind of Achilles heel of the P2P protocol. Once a tracker server goes down, the whole network goes down. BitTorrent programmers came up with a way to discover users without such a server that’s based on the Kademlia DHT technology.
This technology is based on individual BitTorrent clients randomly introducing themselves to each other to establish a kind of distributed directory. However, it was recently showed that one can manipulate some of the data exchanged by BitTorrent clients for trackerless torrenting to introduce oneself to many more clients in the network than necessary and then tell those clients that a popular file is available under a certain IP address.
By manipulating the data being communicated through BitTorrent clients, one can create the appearance of availability for a given file and cause leechers to attempt a download. The leecher would not actually be downloading the intended file, but attacking a target IP without their knowledge. This would result in the flooding of the target host and, in many cases, eventual take-down of the target site.
Nefarious users could utilize publicly available data from torrent sites like The Pirate Bay to find DHT hashes for some of the most popular files and essentially trick some of these downloaders into attacking a certain target. For example, one could tell tens of thousands of users that a fresh version of Tron Legacy (not yet released!) is available at an address that really is the web server of a corporation. All of these users would immediately try to download the file under that address, bombarding the server with requests and possibly taking it down in the process.
Distributed denial of service (DDoS) attacks were most recently used to take down the sites of major credit card companies as part of the Anonymous revenge for actions taken against WikiLeaks. However, users tend to actively take part in a DDoS attack. In the case of this type of exploit, users may not even be aware that they’re bombarding a bank server with bogus requests while they’re trying to download a movie file.
This new technology, termed BotTorrent, would have revolutionary significance not merely in virtue of its creative underpinnings, but in terms of legal responsibility. Clearly, it is unlikely that end-users would prosecuted for carrying out an attack of which they had no knowledge. Furthermore, given the number of unknowing users carrying out the attacks, the magnitude of the attacks would expand massively.
Wikileaks Task Force
The CIA has launched a new task force to assess the impact of Cablegate. The Wikileaks Task Force, , better known by the agency as the acronym WTF, will focus on media exposure and the repercussions of the newest cable releases.
According to a report by the Washington Post, the agency has launched the task force to appraise the impact of thousands of sensitive diplomatic documents and military files hitting the web thanks to WikiLeaks.
Among the task force’s responsibilities is “whether the agency's ability to recruit informants could be damaged by declining confidence in the U.S.
CIA spokesman George Little told the paper that the panel is being led by the CIA's Counterintelligence Center
After Wikileaks published its first batch of classified documents, CIA spokesperson George Little had claimed that the CIA was "unconcerned" about the Wikileaks disclosures. Conversely, on November 8, the following press release emerged:
"When information about our intelligence, our people, or our operations appears in the media, it does incredible damage to our nation’s security and our ability to do our job of protecting the nation."
It seems it was only a matter of time before Little would announce the emergence of a team devoted entirely to the leaks. At present, WTF is taking inventory of all CIA-related information categorized as "classified" but its focus will be that of ascertaining the potential damage to foreign relations that may have been caused by Cablegate leaks.
"It's just a huge vulnerability," an unnamed former high-ranking CIA officer told the Post. "Nobody could carry out enough paper to do what WikiLeaks has done."
Czech version of Wikileaks
WikiLeaks has also been made available on hundreds of mirror sites hosted around the world that duplicate the site's content, including at least three in the Czech Republic
The domain Wikileaks.ch is registered to the Swedish branch of the Pirate Party, an international movement advocating freedom of information and open government.
Jakub Michálek, a board member of Pirate Parties International as well as head of administration for the Czech Pirate Party, told The Prague Post the party is in full support of the WikiLeaks project.
"We strongly believe freedom of the press is a value that deserves protection, and the people should have free access to information. If a situation happens that a server that is a primary source of information for journalists worldwide is attacked, we see it fit the information is copied and distributed to other servers," Michálek said, referring to the party's mirror of Wikileaks on its own website.
It appears that the Czech Pirate Party's attempt to set up its own Wikileaks site isn't going as smoothly as the group hoped. The CPP (Ceska piratska strana) announced the inauguration of its "PirateLeaks" information service earlier this month, to be officially launched on Tuesday. But now the organization says that there will be some delays due to security issues.
"We could host content immediately; that's straightforward," Jakub Michálek, editor-in-chief of PirateLeaks explained to the Czech Position news service. "But what isn't straightforward is insuring 100 percent anonymity for the informers."
The Czech Pirate Party is similar to the Swedish Pirate Party, which advocates for the rights of citizens to share files and publish or access information. The CPP registered as a political entity in June of 2009, and about a year later garnered 0.8 percent of the vote in the Czech Republic
The group has been a big supporter of Wikileaks for quite a while. In May it launched a "pirate copy" of the site—not just a redirect, "but an exact copy, which will be regularly updated," according to a translation of the announcement.
As for establishing its own version of Wikileaks, the CPP describes the project as a "great way to influence regional politics." PirateLeaks will faithfully operate along the Wikileaks methodology—soliciting documents from institutional insiders and getting help from news media in verifying their authenticity.
The big problem, as Michálek sees it, is how to create a portal that protects the identity of sources. And so the party says it will turn to a hosting company owned by the founders of torrent sharing site The Pirate Bay, Gottfrid Svartholm and Fredrik Neij's PeRiQuito (PRQ).
The CPP became a bit more nervous about this project after prominent Czech Republic Christian Democrat Cyril Svoboda declared that PirateLeaks supporters "belong behind bars." In response, CPP activists say they'll petition the government to rename Svoboda (which means "freedom" in Czech) "Cyril Censor."
There is no sure date yet for the launch of PirateLeaks, according to Czech Position.
Operation Payback - The Next Battles
Some of UK's official’s have warned that government websites could become the next target for pro-Wikileaks hackers particularly websites used to file tax returns or claim benefits could be the most vulnerable. So far attacks from the Anonymous group of hacktivists have concentrated on firms perceived to be anti-Wikileaks.
UK web attacks could be likely because Mr Assange, Wikileaks founder has appeared in court where he was granted bail but will remain in prison pending an appeal against the decision. He is wanted by authorities in Sweden for questioning over two sex crimes. He denies the crimes and will fight extradition, his lawyer said.
His mother Christine Assange, who has visited him in prison, said he remained committed to the ideals of Wikileaks. She also passed on his thoughts on the firms which have withdrawn services from the whistle-blowing site. "We now know that Visa, Mastercard, PayPal and others are instruments of US foreign policy. It's not something we knew before," Mr Assange said. The US government has denied that it wrote to individual firms, asking them to stop doing business with Wikileaks.
Some have described the fight between Anonymous, Wikileaks and the US government as the "first infowar" but security experts have downplayed the conflict has being just a demonstration, a protest, nothing more than political theatre - entertaining and influential but not war.
Some have described the fight between Anonymous, Wikileaks and the US government as the "first infowar" but security experts have downplayed the conflict has being just a demonstration, a protest, nothing more than political theatre - entertaining and influential but not war.
Some go as far as to say that this is not a cyberwar because if we are calling it war, we are devaluing what war is. It's a cyber mob. Nevertheless, mobs can be destructive but they tend not to have a long lasting impact.
Meanwhile the US government remains determined to bring Wikileaks and it’s founder to book by exploring a nearly century-old spy law as a way to prosecute Mr Assange.
Controversial documentary director Michael Moore has offered up his help to WikiLeaks founder Julian Assange, both in the form of cash and other resources. The offer came as Assange was finally granted bail from a UK prison—pending Sweden's appeal—on the condition that he obeys a nightly curfew and won't flee the country.
Moore said in an editorial posted to the Huffington Post that he had offered $20,000 of his own money to help bail out Assange. (The offer was made in a letter sent to the court before law enforcement granted Assange his quasi-freedom on Tuesday.) In addition to the money, Moore said that he also wants to offer up his website, servers, domain names, and "anything else I can do to keep WikiLeaks alive and thriving as it continues its work to expose the crimes that were concocted in secret and carried out in our name and with our tax dollars."
"I stand today in absentia with Julian Assange in London and I ask the judge to grant him his release," Moore wrote. "I am willing to guarantee his return to court with the bail money I have wired to said court. I will not allow this injustice to continue unchallenged."
In the cyber war front the main WikiLeaks Web site, WikiLeaks.org, is back up in the U.S. less than 10 days after domain name service provider EveryDNS terminated the whistleblower organization's domain name, citing stability concerns.
In the cyber war front the main WikiLeaks Web site, WikiLeaks.org, is back up in the U.S. less than 10 days after domain name service provider EveryDNS terminated the whistleblower organization's domain name, citing stability concerns.
On Dec. 3, EveryDNS announced that it was terminating the WikiLeaks.org domain name because of repeated distributed denial-of-service (DDoS) attacks that were launched against the Web site soon after it started publishing classified cables from the U.S. Department of State. EveryDNS said it was deactivating WikiLeaks.org because of concerns that the DDoS attacks would cause problems for the nearly 500,000 other Web sites running on EveryDNS's infrastructure.
In response to EveryDNS's actions, WikiLeaks established several new country-level domains, such as WikiLeaks.ch in Switzerland, WikiLeaks.at in Austria and WikiLeaks.cc in Cocos Islands. It then pointed the new domains back to existing IP addresses, or began having the new domains hosted with service providers in different countries.
The restored site is now being hosted by Silicon Valley Web Hosting and is using Dynadot, a San Mateo, California based firm as its registrar and DNS provider, according to Netcraft, an Internet monitoring firm based in the U.K. The site has been up and running since Friday, according to Netcraft. For the moment, the U.S site does not appear to be serving up any content. Instead, it is redirecting users to a mirror site hosted by an Internet service provider in Russia.
But the internet security firm Spamhaus yesterday warned that the site's new incarnation could be riddled with malware run by "Russian cybercriminals". WikiLeaks.org redirects users to a mirror site – mirror.wikileaks.info – which sits within an IP range hosted by the Russian firm Webalta.The main concern is that any WikiLeaks archive posted on a site that is hosted in Webalta space might be infected with malware, since the main wikileaks.org website now transparently redirects visitors to mirror.wikileaks.info, and thus directly into Webalta's controlled IP address space, there is substantial risk that any malware infection would spread widely.
Even so, it is surprising to see WikiLeaks.org being hosted again in the U.S. considering the amount of opposition there has been to its recent actions.
WikiLeaks also heavily reinforced its WikiLeaks.ch domain to avoid a repeat of what happened with EveryDNS. To mitigate the possibility of one DNS provider once again shutting off the domain as EveryDNS had done, WikiLeaks signed up with separate DNS service providers in eight different countries, including Switzerland, Canada and Malaysia. The WikiLeaks.ch site today has a total of 14 different name servers across 11 different networks providing authoritative name services for the WikiLeaks.ch domain. In addition, analysts estimate there are more than 1,000 mirror sites around the world serving up WikiLeaks content so that it is technically almost impossible to entirely remove from the internet.
Operation Payback - Mission Leakflood
Mission Leakflood
Operation Payback have come up with a new way to annoy corporations that have severed their ties with WikiLeaks: bombard them with faxes. As part of its new Leakflood mission, the Anonymous group of 'hacktivists' is encouraging its members to send a large number of faxes to Amazon, MasterCard, Moneybookers, PayPal, Visa and Tableau Software.
In online chats, group members have posted the fax numbers for about a half-dozen corporations and are calling volunteers to fill up the fax machines, using free online fax services such as MyFax.com and FaxZero.com. They're recommending that people use anonymizing software such as the Tor Project to access these sites, so that they cannot be traced by authorities.
This latest campaign by the Anonymous group is analogous to the distributed denial of service attacks it has been carrying out against websites over the past week. In essence, this has turned into a DDoS attack against fax machines. The group started the fax-attacks today at 13:00 GMT and published a list of target fax numbers in their call to arms:
"The enemy is adapting to our strategies, Gentlemen, but they are a lumbering bureaucracy. We can change faster," the group said in a note being circulated on its chat servers Monday.
The activists are being encouraged to send faxes of random WikiLeaks cables, letters from Anonymous, Guy Fawkes, and the WikiLeaks logo to the target fax numbers all day long. It is not clear how many people are taking part in the attacks, but an IRC channel set up to provide information about the campaign contained 73 users just a few hours after the fax-attacks started.
The loosely organized group behind Operation Payback, called Anonymous, has tried this tactic before. In January 2008 it encouraged members to fax-bomb the Church of Scientology, another of its favorite targets.
Although Operation Payback's attacks have gained a lot of media attention, they have had little effect on their targets' core businesses. MasterCard said that some of its SecureCode transaction processing was slowed down last week, but the back-end transaction systems used by Visa and MasterCard have been unaffected by the attacks. Paypal's Paypal.com website went down on Thursday, but the company said that the servers it uses to process transactions were virtually unaffected.
The attacks aren't difficult to thwart, but they do cost money as companies have to scramble and harden their infrastructure. In the meantime, they make it hard for customers to reach the company. Those websites are usually the first port of call for anyone who wants to use those online services.
The fax attacks look like they could be an annoyance, and they appear to be having some effect. Anonymous has posted a list of numbers that it says are no longer responsive.
As well as dishing out attacks, the group has also found itself under attack for supporting WikiLeaks. Many users were knocked off its IRC network after its servers came under attack this morning. It is also understood that the anonops.eu domain (which used to announce the locations of IRC servers and the current attack target) has also come under attack and is currently unavailable.
Real-time performance graphs for websites that have been involved (or may become involved) in the WikiLeaks attacks can be monitored at http://uptime.netcraft.com/perf/reports/performance/wikileaks; however, Netcraft is not monitoring any of the fax machines.
Cyber War V - The Aftermath
Operation Payback
The wave of electronic assaults, referred to as "Operation Payback" led by the Anonymous group of activists as an effort to conduct denial of service attacks against a wide range of targets has experienced something of a setback and is now changing course. Yesterday's arrest of a Dutch teenager has caused some difficulties for the group as well, as he was apparently the operator of an IRC server coordinating the attacks. The result: a change in course and what appears to be diminished enthusiasm on the part of 4chan denizens who make up the Anonymous collective.
These attacks were aimed at the home sites of the credit card companies. Those sites have high profiles but relatively low traffic levels -- traffic levels that make them more vulnerable to a distributed denial of service (DDoS) attack. Such attacks deliberately spike the traffic to a site and make it inaccessible. But those were just are their public-facing websites, not the transaction processing.
While the headlines Operation Payback has been able to generate with its attacks may be giving the credit card companies a black eye and are a source of embarrassment, they are distorting the actual security threat to the firms' financial systems. Where it counts, which is making sure that when you and I are at the mall buying gifts for our family for Christmas, they've got an amazingly robust infrastructure.
Operation Payback's attacks on Visa and MasterCard were undertaken in retaliation for the companies' decision to refuse to process donations to Wikileaks, a site that most recently made waves by leaking hundreds of thousands of private U.S. State Department messages, some of which were classified as "Secret."
PayPal, an online financial transaction company, took similar action, but its main site did not come under attack. They didn't try to take out PayPal itself because PayPal is way too large and distributed and able to resist the attack, and it wouldn't look good for the attacker so they went after Paypal's blog instead because it was an easier target.
Although the transaction systems of the credit card companies may have been insulated from the denial of service attacks on their home sites, the assaults may have some financial consequences for the firms. Both businesses have programs -- Verified By Visa and MasterCard SecureCode -- that require additional authentication when making online purchases with merchants participating in those programs. Those systems are being affected by these denial of service attacks because they rely on MasterCard's and Visa's websites to be there to type in your extra security code. There is the potential of holiday shoppers shopping online not being able to purchase anything with their MasterCard or Visa, and so it could hit the pocketbooks over at the credit card companies.
Operation Leakspin
But Operation Payback is yesterday's news. Today, it's all about Operation Leakspin. Now apparently Anonymous switched from trying to disrupt anti-Wikileaks sites to trying to spread the info from Wikileaks' secret diplomatic cables in as many ways as possible. This new tactic is called Operation Leakspin.
The idea behind Leakspin is to pick out some of the less-publicized Wikileaks info and post it in innocuous locations, in YouTube videos and on message boards. Videos with popular keywords like "Bieber" could turn out be Anonymous members reading from the secret diplomatic cables. Why the sudden change in tactics? Because the mission all along has been to keep the Wikileaks documents online. "They don't fear the LOIC. They fear exposure," says the Op Leakspin poster.
This morning, Anonymous issued a press release in an attempt to explain its new position. The release states that Anonymous has no interest in compromising personal information or credit card details, but rather that its attacks on financial companies are motivated by a desire to draw attention to the way in which they are hurting WikiLeaks—taking "symbolic action" against the companies' "public faces." The announcement also recognizes that the group has not been doing a good job of explaining its motivation so far.
The authors of the press release also sought to distance themselves from calls made on Twitter yesterday to attack amazon.com—an attack that did not actually occur. A denial of service attack on Amazon was unlikely to succeed—the very reason that WikiLeaks itself used the company for its hosting for a brief period—but more than this, the writers say that such an attack would "affect people such as consumers in a negative way and make them feel threatened by Anonymous." As such, it would be counterproductive and "in bad taste."
In the meantime, several of the Anonymous IRC servers are offline, with some "down for maintenance," which could very well indicate that the group is looking for new hosting. At the very least, they're experiencing serious DNS issues. There also seems to be little enthusiasm for the new approach on 4chan.
Operation Payback has also been slowed down by Twitter and Facebook banning pages that broadcast Anon's plans and calls to action. Although Twitter has said they're not blocking Wikileaks tweets from the trending topics list, they did shut down the Anonymous Operations Twitter account. Facebook took down the equivalent page on its site, too. Naturally, several more have popped up in their place. There are conflicting claims about whether the US government has put pressure on financial services and social media sites to stifle support for Wikileaks.
High Orbit Ion Cannon
But this might not be the end of the DDoS Attacks, today a new tool was released and a new wave of attacks was somehow initiated using the High Orbit Ion Cannon. This new tool is supposed to be more effective, less prone to detection hence theoretically capable of greater damage to targeted websites.
Cyber War IV - Operation Payback explained
These kind of hacking campaigns are not a new phenomenon triggered by the Wikileaks situation. Just to mention a well-known example, back in 2003, the Recording Industry Association of America (RIAA) had their site collapsed due to a series of online attacks after they’d launched a joint anti-file piracy campaign together the Motion Picture Association of America (MPAA). Now we have this so called “Operation Payback”, a new initiative allegedly from the same group of hackers that performed the attacks in 2003.
It’s believed that other hacker groups have joined in on the efforts to ally themselves with WikiLeaks and attack those who’ve attacked out against WikiLeaks. Nobody on the outside knows just how big this network spans and especially if they’ve been banded together with communities like 4chan, it could very well be one of the largest unified hacking campaigns to date.
This type of attack typically involves flooding a target website with data. The attackers hope to overwhelm it in one way or another so it cannot serve its legitimate users. As its name implies it aims to deny service to those visitors.
How are the attacks made?
Using Twitter and probably hidden IRC channels, the group has managed coordinate their attacks in a very effective way. The majority of the attacks so far have all been mass DDoS (Distributed Denial-of-Service) attacks which on a big scale and have been effective in collapsing the websites of these organizations. In case you're unaware of the type of attack this is, it's a method that calls on multiple computers (usually networked as slave units) to connect all at once and continuously to the victim of the attack, causing their servers to collapse due to the weight of traffic demands.
There are many types of DDoS attacks; some exploit the basic protocols of the internet that define how your web browser talks to the webpage you want to visit while other attacks send fragments of data packets to a target so it spends all its time putting them back together rather than sending data to visitors. Against sites with a low bandwidth link to the wider web simply sending lots of data traffic can choke the connection and cut it off.
In essence, what is happening is that lots and lots of individuals are hammering specific websites with TCP or UDP packets or HTTP requests. There are only so many resources to go around, which means that with enough individuals involved, even large websites can be taken down very quickly.
In essence, what is happening is that lots and lots of individuals are hammering specific websites with TCP or UDP packets or HTTP requests. There are only so many resources to go around, which means that with enough individuals involved, even large websites can be taken down very quickly.
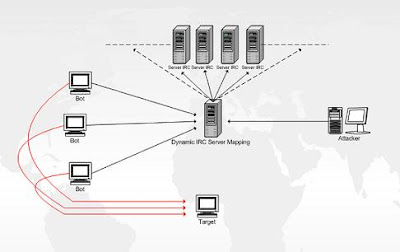
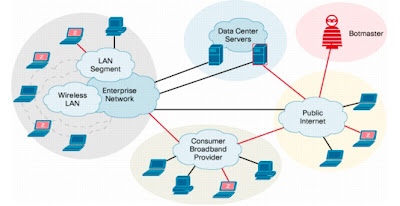
The first denial of service attacks typically came from a single source. Now the data bombardment is typically carried out by lots of computers, usually running Windows, all over the world, hence distributed. Most attacks are carried out through a botnet.
Botnets are groups of computers, unwittingly linked together via the internet, that can be remotely controlled to perform tasks. Typically they send out spam email, perform DDoS attacks, and gather personal information. Botnets are typically created through virus infection, or by installing malicious software (known as malware) on your machine. Malware can take many forms but are typically referred to as a 'trojan'. Named after the legendary Trojan horse, it is a piece of malicious code that hides inside another piece of software (in this instance illegally downloaded copies of software).
Most of the participants in Operation Payback are not hackers — at least not in the true sense of the word. Instead, these users are using computer programs — or more recently, simply visiting websites — in order to stage their attack.
Anonymous is using a botnet but one that is slightly different to the usual. The botnet is made up of machines that have been actively enrolled in it by their owners downloading and installing Anonymous' attack tool - known as the Low Orbit Ion Cannon (LOIC).
What is a botnet?
Botnets are groups of computers, unwittingly linked together via the internet, that can be remotely controlled to perform tasks. Typically they send out spam email, perform DDoS attacks, and gather personal information. Botnets are typically created through virus infection, or by installing malicious software (known as malware) on your machine. Malware can take many forms but are typically referred to as a 'trojan'. Named after the legendary Trojan horse, it is a piece of malicious code that hides inside another piece of software (in this instance illegally downloaded copies of software).
As the user installs the software, it is also installing the trojan program unware of the fact that might be creating a new zombie computer to be part of a botnet controled by who knows who....
Most of the participants in Operation Payback are not hackers — at least not in the true sense of the word. Instead, these users are using computer programs — or more recently, simply visiting websites — in order to stage their attack.
Anonymous is using a botnet but one that is slightly different to the usual. The botnet is made up of machines that have been actively enrolled in it by their owners downloading and installing Anonymous' attack tool - known as the Low Orbit Ion Cannon (LOIC).
This tool, which was purportedly originally created to stress test networks, is written in C# and can be downloaded off open source code repositories like Github and Sourceforge.
LOIC can be used to target a website the user inputs, or using an option called Hive Mind, to connect to IRC or even Twitter, and grab information for a targeted web attack. Because C# will only work on Windows computers out of the box (Mac and Linux users have to install additional libraries and do extra configuration), a Java port of LOIC also exists. The most recent variant of LOIC is a new proof of concept that is floating around called JS LOIC. The “JS” in the title stands for JavaScript. This proof of concept, which doesn’t appear to have as many features as LOIC or Java LOIC — and may also be easier to stop — is actually pretty clever.
Rather than requiring a user download program to run, someone can just visit a web page with a single HTML file and press a button to carry out their part of an attack. On the one hand, the trick of using JavaScript to carry out this kind of flooding attack is pretty clever. On the other hand, it’s also pretty scary.
From what we can gather, the majority of the attacks on Operation Payback targets are not coming from web clients. However, that could change. We would caution users against clicking on any links claiming to aid in this series of attacks. Not only is willfully participating in a DDoS illegal in many countries, you never know what is behind the file you download or what action clicking on that web button could trigger.
As with many other aspects of the WikiLeaks saga, the distributed and de-centralized nature of the Internet means that shutting down all mirrors for documents — or even for attack tools — is an exercise in futility.
This is easily the most public and mainstream hacking campaign to date and so far it must be said, has been largely successful. A spokesperson for the group behind Operation Payback posted that they’d attack all of those who were “bowing down to government pressure”.
So what does this say about the power of the internet? Nothing really that experts didn’t know about. But for the general public and for the media as a whole, I think it’s come to quite a shock to them knowing that hackers could be so influential and on the frontline of the news for a sustained period of time. Most people’s impressions of your average hacker is that of one who sits around and steals your credit card number and whilst this is still a major problem, it does put things into perspective when groups such as Anon manage to bring down Goliath companies like Mastercard and Swiss FinancePost to their knees.
Small defacement attacks by political reasons, or just for the fun of it, are very common and happen every day but this is a completely new phenomenon, we are now dealing with a potentially global cyber power and cyber war can trigger some heavy legislative responses from governments worldwide.
Cyber War III - Change in Tactics?
'Coldblood', a member of the group Anonymous, told a BBC reporter why he views its attacks on Visa and Mastercard as defence of Wikileaks. Web attacks carried out in support of Wikileaks are being wound down as activists consider changing tactics. Attacks against Amazon were called off late on 9 December and re-directed towards net payments firm Paypal and its computer systems which, according to a status page, has intermittently suffered "performance issues" ever since.
There have also been calls for attacks on official Dutch websites following the arrest of a 16-year-old boy suspected of involvement in the online campaign. But early today Moneybookers was chosen as the next target and its site was occasionally unreachable from about 1100 GMT.
The chances of success could be boosted by a new version of LOIC written in web programming language Javascript that allows anyone with a browser, including on a mobile phone, to launch attacks. However, defences against the attacks were being drawn up as security firms scrutinise the code behind LOIC to work out how attacks happen. Some suggest that well-written firewall rules would be able to filter out most of the harmful traffic.
The LOIC tool has been downloaded more than 46,000 times but, said Anonymous activists in a tweet, this did not translate into enough people using it to knock the retail giant off the web
One of those activists said he had a botnet of 30,000 machines under his control that he was planning to use on behalf of Wikileaks. A botnet is a network of hijacked home computers that have been compromised by their owners visiting a booby-trapped webpage that installs code to hand over control to a hi-tech criminal. A botnet with 30,000 machines in it is considered to be about average size. Most of the spam sent around the net is funnelled through machines that are in botnets.
There are also suggestions that the Anonymous group might be about to drop the web attacks in favour of another tactic. Its use of the term Anonymous comes from a series of websites frequented by members, such as the anarchic image board 4Chan. These allow users to post without having to register or provide a name. As a result, their comments are tagged "Anonymous".
A message posted on the 4chan image board, out of which Anonymous has grown, suggests dropping LOIC in favour of publicising information in the diplomatic cables that Wikileaks is releasing. Searching for the less-well publicised cables and spreading the information they contain around the web could be more effective than simply knocking out sites deemed to be enemies of Wikileaks, it said.
The message also suggests using misleading tags on posts and YouTube videos to trick people into reading or viewing the information.
"They don't fear the LOIC, they fear exposure," read the message.
Cyber War II - The Lone Wolf
The cyberattacks in Assange's defense appear to have been coordinated by Anonymous, a loosely affiliated group of activist computer hackers who have singled out other groups before, including the Church of Scientology and Gene Simmons of the rock band Kiss, who spoke out against file sharing. Last weekend, members of Anonymous vowed in two online manifestoes to take revenge on any organization that lined up against WikiLeaks in an effort called "Operation Payback."
Anonymous has an enemy in the hacking community, however: a self-proclaimed "hacktivist for good" who calls himself The Jester. He has claimed responsibility for taking down WikiLeaks' website several times since it started posting confidential State Department cables Nov. 28. The Jester, who describes himself as a patriotic hacker with a military background, claims other like-minded hackers have approached him to help.
Anonymous brings hackers into secure chat rooms at encrypted websites where potential targets are identified and hackers are encouraged to attack. On Wednesday, one of the Anonymous chat rooms, anonops.net, was under "massive" attack" probably by this guy, the Jester.
The Jester came to the attention of cyber security experts this year when he disabled several websites run by Islamic extremists. He told computer forensics expert Richard Stiennon in an e-mail in January that he had served in a "rather famous unit" inAfghanistan
The Jester uses a disruption method that cyber experts had not seen before. The Jester wrote a program called XerXeS that clogs up a website like WikiLeaks.org, instructing it to launch continual requests for information, so the website is too busy to load.
The Anonymous group, like most hackers, shuts down websites by launching what are known as distributed denial of service attacks. Usually, these attacks are launched from a network of thousands of unsuspecting computers connected to the Internet.
What's more, Anonymous' computing base is located on "bulletproof" hosts inRussia
Anonymous has an enemy in the hacking community, however: a self-proclaimed "hacktivist for good" who calls himself The Jester. He has claimed responsibility for taking down WikiLeaks' website several times since it started posting confidential State Department cables Nov. 28. The Jester, who describes himself as a patriotic hacker with a military background, claims other like-minded hackers have approached him to help.
Anonymous brings hackers into secure chat rooms at encrypted websites where potential targets are identified and hackers are encouraged to attack. On Wednesday, one of the Anonymous chat rooms, anonops.net, was under "massive" attack" probably by this guy, the Jester.
The Jester came to the attention of cyber security experts this year when he disabled several websites run by Islamic extremists. He told computer forensics expert Richard Stiennon in an e-mail in January that he had served in a "rather famous unit" in
The Jester uses a disruption method that cyber experts had not seen before. The Jester wrote a program called XerXeS that clogs up a website like WikiLeaks.org, instructing it to launch continual requests for information, so the website is too busy to load.
The Anonymous group, like most hackers, shuts down websites by launching what are known as distributed denial of service attacks. Usually, these attacks are launched from a network of thousands of unsuspecting computers connected to the Internet.
What's more, Anonymous' computing base is located on "bulletproof" hosts in
Cyber War
I believe we are witnessing what could be the first real cyber war of the XXI century between the supporters of Wikileaks and all the institutions that somehow oppose to it or have withdrawn its support.
Despite several attacks targeting the site wikileaks.org among which are massive Denial of Service attacks, the end of the domain registration, the loss of Amazon hosting services and also the end of services provided by Paypal, Visa and MasterCard, the reality is that the site has shown a surprising vitality and is becoming a real case study in terms of resistance to such attacks.
Before the revelation of the last batch of secret documents, the contents of the site were hosted in two Swedish and one French service providers. Subsequently, the same content was also housed in the cloud storage service from Amazon but this firm quickly changed his mind claiming breach of the terms of service.
Following Amazon's actions the problems with the ISP begun that culminated with the end of the domain registration wikileaks.org by the DNS service provider, the company EveryDNS.
In retaliation, Wikileaks has created various national level domains subsequently redirecting the IP addresses in some cases or using the services of ISPs in several countries.
In order to prevent a repetition of what happened with EveryDNS, ie, having the site dependent on a single DNS service provider, Wikileaks is now using DNS services in eight different countries.
This geographical dispersion makes the site already extremely difficult to shut down, but for now, the site content is hosted mainly in European servers, as soon as the dispersion becomes worldwide, then any attempts to close the site will face increasing challenges.
Moreover, in recent days thousands of mirrors of the original site appeared which means that the content is already so widespread in several domains of the Internet that now escapes the jurisdiction of any legislative body and even with a concerted global effort will be impossible to prevent fragments of this information from reappearing.
The targets of the attacks by this phalanx of supporters have been the Amazon, MasterCard, PayPal and the Swiss firm PostFinance sites due to the freezing of Wikileaks’ accounts.
At the same time, a rising of a global army of activists and Wikileaks supporters is on the march growing every day both in numbers and strength by adding the power of botnets or using tools freely available and free.
Synchronizations are being made using Twitter and IRC (Internet Relay Channel) networks where a group recently emerged began the so called "Operation Payback."
But if so far the bulk of the column has been manned by anonymous volunteers with LOIC, now we are in the stage where this army will be reinforced with the battalions of existing botnets of computers already infected and controlled by groups of hackers who are responding to the call to meet the new defensive measures implemented by the targeted sites.
This cyber war may change the face of the Internet as we know it ...
Manhunt
Wikileaks founder arrested by British police
The issue of Wikileaks, about which much has been written, should not be considered lightly, so let’s see:
-Who is really behind Mr. Assange?
-To whom it serves all of this mess?
-Who are the sources capable of providing information at this level?
-What are the real effects caused by all this?
In today's world it’s absolutely essential that we ask ourselves about the causes and consequences of all that we hear in the media, from the smallest sound bite to the biggest scandal.
Freedom of expression should not be an absolute value with the authority to impose itself on everyone and everything so blindly, without conscience or remorse.
Freedom of expression?
What is that exactly? What are the limits? Are there any at all?
I confess I have mix feelings on the existence of the site but the question remains: Why now? Who moves in the background of all this giant conspiracy? The site's existence might be disputable but one thing is unquestionable; the world will never be the same again!
I confess I have mix feelings on the existence of the site but the question remains: Why now? Who moves in the background of all this giant conspiracy? The site's existence might be disputable but one thing is unquestionable; the world will never be the same again!
Subscribe to:
Comments (Atom)