These kind of hacking campaigns are not a new phenomenon triggered by the Wikileaks situation. Just to mention a well-known example, back in 2003, the Recording Industry Association of America (RIAA) had their site collapsed due to a series of online attacks after they’d launched a joint anti-file piracy campaign together the Motion Picture Association of America (MPAA). Now we have this so called “Operation Payback”, a new initiative allegedly from the same group of hackers that performed the attacks in 2003.
It’s believed that other hacker groups have joined in on the efforts to ally themselves with WikiLeaks and attack those who’ve attacked out against WikiLeaks. Nobody on the outside knows just how big this network spans and especially if they’ve been banded together with communities like 4chan, it could very well be one of the largest unified hacking campaigns to date.
This type of attack typically involves flooding a target website with data. The attackers hope to overwhelm it in one way or another so it cannot serve its legitimate users. As its name implies it aims to deny service to those visitors.
How are the attacks made?
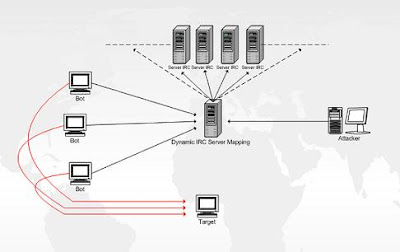
Using Twitter and probably hidden IRC channels, the group has managed coordinate their attacks in a very effective way. The majority of the attacks so far have all been mass DDoS (Distributed Denial-of-Service) attacks which on a big scale and have been effective in collapsing the websites of these organizations. In case you're unaware of the type of attack this is, it's a method that calls on multiple computers (usually networked as slave units) to connect all at once and continuously to the victim of the attack, causing their servers to collapse due to the weight of traffic demands.
There are many types of DDoS attacks; some exploit the basic protocols of the internet that define how your web browser talks to the webpage you want to visit while other attacks send fragments of data packets to a target so it spends all its time putting them back together rather than sending data to visitors. Against sites with a low bandwidth link to the wider web simply sending lots of data traffic can choke the connection and cut it off.
In essence, what is happening is that lots and lots of individuals are hammering specific websites with TCP or UDP packets or HTTP requests. There are only so many resources to go around, which means that with enough individuals involved, even large websites can be taken down very quickly.
In essence, what is happening is that lots and lots of individuals are hammering specific websites with TCP or UDP packets or HTTP requests. There are only so many resources to go around, which means that with enough individuals involved, even large websites can be taken down very quickly.
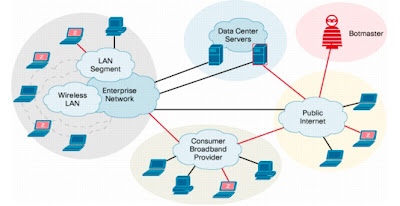
The first denial of service attacks typically came from a single source. Now the data bombardment is typically carried out by lots of computers, usually running Windows, all over the world, hence distributed. Most attacks are carried out through a botnet.
Botnets are groups of computers, unwittingly linked together via the internet, that can be remotely controlled to perform tasks. Typically they send out spam email, perform DDoS attacks, and gather personal information. Botnets are typically created through virus infection, or by installing malicious software (known as malware) on your machine. Malware can take many forms but are typically referred to as a 'trojan'. Named after the legendary Trojan horse, it is a piece of malicious code that hides inside another piece of software (in this instance illegally downloaded copies of software).
Most of the participants in Operation Payback are not hackers — at least not in the true sense of the word. Instead, these users are using computer programs — or more recently, simply visiting websites — in order to stage their attack.
Anonymous is using a botnet but one that is slightly different to the usual. The botnet is made up of machines that have been actively enrolled in it by their owners downloading and installing Anonymous' attack tool - known as the Low Orbit Ion Cannon (LOIC).
What is a botnet?
Botnets are groups of computers, unwittingly linked together via the internet, that can be remotely controlled to perform tasks. Typically they send out spam email, perform DDoS attacks, and gather personal information. Botnets are typically created through virus infection, or by installing malicious software (known as malware) on your machine. Malware can take many forms but are typically referred to as a 'trojan'. Named after the legendary Trojan horse, it is a piece of malicious code that hides inside another piece of software (in this instance illegally downloaded copies of software).
As the user installs the software, it is also installing the trojan program unware of the fact that might be creating a new zombie computer to be part of a botnet controled by who knows who....
Most of the participants in Operation Payback are not hackers — at least not in the true sense of the word. Instead, these users are using computer programs — or more recently, simply visiting websites — in order to stage their attack.
Anonymous is using a botnet but one that is slightly different to the usual. The botnet is made up of machines that have been actively enrolled in it by their owners downloading and installing Anonymous' attack tool - known as the Low Orbit Ion Cannon (LOIC).
This tool, which was purportedly originally created to stress test networks, is written in C# and can be downloaded off open source code repositories like Github and Sourceforge.
LOIC can be used to target a website the user inputs, or using an option called Hive Mind, to connect to IRC or even Twitter, and grab information for a targeted web attack. Because C# will only work on Windows computers out of the box (Mac and Linux users have to install additional libraries and do extra configuration), a Java port of LOIC also exists. The most recent variant of LOIC is a new proof of concept that is floating around called JS LOIC. The “JS” in the title stands for JavaScript. This proof of concept, which doesn’t appear to have as many features as LOIC or Java LOIC — and may also be easier to stop — is actually pretty clever.
Rather than requiring a user download program to run, someone can just visit a web page with a single HTML file and press a button to carry out their part of an attack. On the one hand, the trick of using JavaScript to carry out this kind of flooding attack is pretty clever. On the other hand, it’s also pretty scary.
From what we can gather, the majority of the attacks on Operation Payback targets are not coming from web clients. However, that could change. We would caution users against clicking on any links claiming to aid in this series of attacks. Not only is willfully participating in a DDoS illegal in many countries, you never know what is behind the file you download or what action clicking on that web button could trigger.
As with many other aspects of the WikiLeaks saga, the distributed and de-centralized nature of the Internet means that shutting down all mirrors for documents — or even for attack tools — is an exercise in futility.
This is easily the most public and mainstream hacking campaign to date and so far it must be said, has been largely successful. A spokesperson for the group behind Operation Payback posted that they’d attack all of those who were “bowing down to government pressure”.
So what does this say about the power of the internet? Nothing really that experts didn’t know about. But for the general public and for the media as a whole, I think it’s come to quite a shock to them knowing that hackers could be so influential and on the frontline of the news for a sustained period of time. Most people’s impressions of your average hacker is that of one who sits around and steals your credit card number and whilst this is still a major problem, it does put things into perspective when groups such as Anon manage to bring down Goliath companies like Mastercard and Swiss FinancePost to their knees.
Small defacement attacks by political reasons, or just for the fun of it, are very common and happen every day but this is a completely new phenomenon, we are now dealing with a potentially global cyber power and cyber war can trigger some heavy legislative responses from governments worldwide.




4 comments:
Great informative post, thanks so much for sharing your thoughts on this.
Please visit once at ddoscube.com.
Thank you for the great post.
Prancer is a pre-deployment and post-deployment multi-cloud validation framework for your Infrastructure as Code (IaC) pipeline and continuous compliance in the cloud.
**HIGH CREDIT SCORES SSN FULLZ AVAILABLE**
>For tax filling/return
>SSN dob DL all info included
>For SBA & PUA filling
>Fresh spammed & Fresh database
**TOOLS & TUTORIALS AVAILABLE FOR HACKING SPAMMING CARDING CASHOUTS CLONING**
=>Contact 24/7<=
Telegram> @killhacks
ICQ> 752822040
Skype> Peeterhacks
FRESHLY SPAMMED
VALID INFO WITH VALID DL EXPIRIES
*All info included*
NAME+SSN+DOB+DL+DL-STATE+ADDRESS
Employee & Bank details included
CC & CVV'S ONLY USA AVAILABLE
SSN+DOB
SSN+DOB+DL
High credit fullz 700+
(bulk order negotiable)
*Payment in all crypto currencies will be accepted
->You can buy few for testing
->Invalid info found, will be replaced
->Serious buyers contact me for long term business & excellent profit
->Genuine & Verified stuff
TOOLS & TUTORIALS AVAILABLE FOR
(Carding, spamming, hacking, scripting, scam page, Cash outs, dumps cash outs)
Ethical Hacking Tools & Tutorials
Kali linux
Facebook & Google hacking
SQL Injector
Bitcoin flasher
Viruses
Keylogger & Keystroke Logger
Logins Premium (Netflix, coinbase, FedEx, PayPal, Amazon, Banks etc)
Paypal Logins
Bulk SMS Sender
Bitcoin Cracker
SMTP Linux Root
DUMPS with pins track 1 and 2 with & without pin
Smtp's, Safe Socks, rdp's, VPN, Viruses
Cpanel
Php mailer
Server I.P's & Proxies
HQ Emails Combo (Gmail, yahoo, Hotmail, MSN, AOL, etc)
->Serious buyers are always welcome
->Big discount in bulk order
->Offer gives monthly, quareterly, half yearly & yearly)
->Hope we do a great business together
CONTACT 24/7
Telegram> @killhacks
ICQ> 752822040
Skype> Peeterhacks
BEYOND AVERAGE CRYPTO RECOVERY;THE SYNACK HACKERS EXPERIENCE
Not a while back, I found myself in a major pickle when I realized I had lost all my precious (12 BTC) and $190K worth of Ethereum. I was devastated and had no clue what to do. I had worked my body off to achieve all that because I wanted to build up schools in Africa and do some water projects there to help people have a better life. But then, I stumbled upon Synack Hackers and let me tell you, they were a game-changer. Their team of experts not only understood the complexity of my situation but also showed genuine care and dedication in helping me out. They were like superheroes in the crypto world! From the get-go, the Synack Hackers team was extremely responsive and attentive. They patiently listened to my concerns and assured me that they would do everything in their power to recover my lost BTC. And boy, did they deliver! Their technical expertise and cutting-edge tools were truly impressive. They left no stone unturned in their quest to track down and restore my lost funds. Throughout the entire process, they kept me in the loop, providing regular updates and answering all my questions. Thanks to Synack Hackers tireless efforts, I am thrilled to say that I successfully recovered my lost BTC and Ethereum. It's like a weight has been lifted off my shoulders! I can't thank them enough for their professionalism, expertise, and genuine care.
If you ever find yourself in a similar situation, I highly recommend reaching out to Synack Hackers.. They are the real deal when it comes to recovering lost cryptocurrency. Trust me, you won't be disappointed. Yes! Projects commencing soon in Africa. Get in touch with them via information listed:
Mail; Synackhackers (@) proton (.) me
Post a Comment